Multiple WordPress websites, some of them advertising financial services, have been compromised by cybercriminals to leak authentication credentials to a third party server.
Security researchers from Zscaler found a set of 18 websites that serve a malicious JavaScript on the login page and steals the access password. The theft is performed without raising any suspicion to the user as they are redirected to an authenticated session of the WordPress site.
Backdoor code activates on login action
According to the list of compromised websites compiled by Zscaler, it seems that the attackers are indiscriminate about their targets.
Some of the locations promote beauty products, while others provide financial planning services; in other cases, the websites deliver news from different domains or promote artistic events.
The researchers say that the website impacted run a backdoor code that becomes active when the user submits the login data. The credentials are then encoded and delivered to a machine via a GET request.
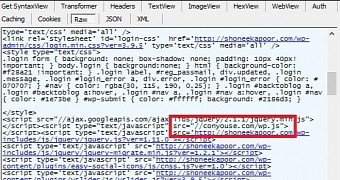
According to the analysis, the destination of the stolen information is “conyouse.com,” which also acts as the host for the malicious JavaScript.
“The form containing the username and password input box has a fixed name as ‘loginform’ in all WordPress sites. The preventDefault event method is used to cancel the submit event for ‘loginform’ entity and execute the alternate code which is present in this file. The login credential string is serialised and encoded in a Base64 format,” the researchers said in a blog post.
Admins should update to the latest WordPress version
Sameer Patil from Zscaler notes in a reply to a comment that websites running WordPress 4.1.5 and the latest 4.2.2 have been identified to be exploited in the campaign.
Patil added that the initial attack vector remains unknown at the moment. However, he advises Wordpress administrators to update the content management system in order to benefit from the latest security updates.
On Thursday, WordPress received an update to version 4.2.2, which addresses a DOM-based bug that can be exploited through the “example.html” file the Genericons package present in multiple plugins as well as in the default theme Twenty Fifteen.
 14 DAY TRIAL //
14 DAY TRIAL //