Build 4.0.1 of WordPress has been released to fix a serious cross-site scripting (XSS) flaw that impacts all versions of the CMS (content management system) earlier than 4.0, which account for 85.5% of the WordPress installations.
The vulnerability has passed unobserved for about four years, as it was introduced in version 3.0 of the CMS, released in 2010. Discovered by Jouko Pynnonen from Finnish IT company Klikki Oy, the vulnerability allows execution of arbitrary JavaScript code injected in comment boxes.
The weakness allows creating a new admin account
The commands in the code are run with administrative privileges and are triggered the moment the target tries to view the malcrafted comment.
One attack scenario is to hide the malicious JavaScript between different URLs in a comment. The text passes into the moderation queue and commands are executed upon reviewing the comment.
This way, the malicious intent cannot be spotted by other users or through search engines, since the target is the only party with access to the comment.
An explanation from Klikki Oy informs that all operations are carried out in the background without drawing attention in any way. An attacker could execute commands for changing the password of the current user, creating a new admin account.
More worryingly, there is the possibility to add malicious PHP code on the server through the plug-in editor, and execute it immediately with an Ajax request. This could lead to the attacker gaining operating system level access on the server.
Klikki Oy researchers say that if the malcrafted message is approved in the Dashboard, the exploit is “triggered by any user viewing the targeted blog posting or page, with their corresponding privileges.”
All WordPress site admins should apply the latest update
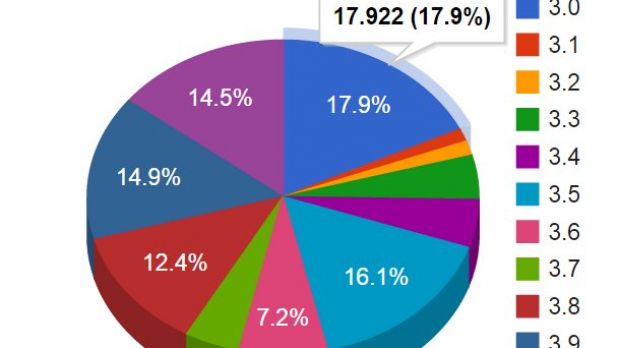
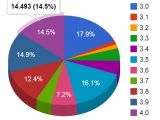
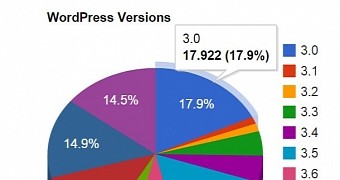
As per usage statistics from WordPress, only 14.5% of the total installations of the blog platform run version 4.0, which is not affected by this bug. Most of the administrators seem to still prefer the buggy builds 3.0 (17.9), 3.5 (16.1%), and 3.9 (14.9%).
Users are advised to upgrade to the latest version available for the CMS as soon as possible, since security patches for other glitches have been implemented.
Build 4.0.1 also eliminates three other XSS risks that could allow a third party to compromise a website, a cross-site request forgery (CSRF) attack that would trick users into changing the password, and an issue that may lead to denial-of-service when checking passwords.
The WordPress advisory informs that developers implemented protection against server-side request forgery attacks when the CMS makes HTTP requests.
 14 DAY TRIAL //
14 DAY TRIAL //