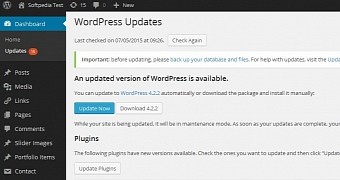
The maintainers of WordPress have released a critical security update for the content management system to version 4.2.2 that eliminates a cross-site scripting (XSS) bug present in all plugins and themes with the Genericons icon font package.
The vulnerability is present in popular components that are available in millions of websites, and could be leveraged to hijack them if certain conditions are met.
Glitch is present in default WordPress theme
The Genericons package includes an HTML file called “example.html,” which is vulnerable to a DOM-based XSS attack. The threat actor can craft a link pointing to this resource and provide malicious JavaScript code that is executed in the context of the web browser.
If the link is accessed by an authenticated administrator, there is the possibility of taking over the website.
On Thursday, all themes and plugins published on WordPress.org were updated to remove the HTML file that allowed the security breach.
One of the themes affected is Twenty Fifteen, which was downloaded almost 73,000 times. However, it is also present in the default WordPress package and is thus installed automatically with the CMS.
Buggy file removed automatically following proactive scans
Jetpack, a plugin with more than 1 million active installations, was also updated and no longer includes the “example.html” file in the Genericons package.
“To help protect other Genericons usage, WordPress 4.2.2 proactively scans the wp-content directory for this HTML file and removes it,” says a security advisory from the maintainers of the CMS on Thursday.
Website administrators are urged to switch to the new version as soon as possible. If this action cannot be performed with the utmost urgency, the security flaw can be mended by deleting the “example.html” file in the “genericons” folder.
Alternatively, access to this resource can be blocked via security products protecting the website (firewall, IDS).
According to Sucuri, the flaw is currently exploited in the wild, although the proof-of-concept they’ve seen does not compromise websites and only causes a JavaScript alert.
 14 DAY TRIAL //
14 DAY TRIAL //