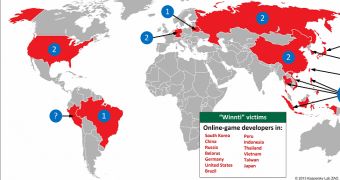
Security experts continue to analyze pieces of malware from the Winnti family, which are mainly used by a Chinese cybercriminal group to target South East Asian organizations from the video gaming sector. Trend Micro researchers have uncovered a new backdoor that’s possibly used in targeted attacks.
The threat, dubbed “Bkdr_Tengo.A,” passes itself off as a legitimate system DLL file called winmm.dll.
This is not uncommon for Winnti malware. However, the backdoor is interesting because Aheadlib has been abused to make it look like a legitimate system library.
Aheadlib is a legitimate analysis tool that can be used to construct C code from DLL files. The tool is capable of hooking all the functions provided by the initial library.
While Aheadlib is a great utility for malware analysis, it can also be used for more nefarious purposes by cybercriminals.
Fortunately, in this case, the malicious file is not encrypted, so Trend Micro experts have been able to easily analyze it.
They report that the threat is designed to steal Microsoft Office, TIFF and PDF files from USB drives attached to an infected system. It also allows cybercriminals to take control of an infected device.
 14 DAY TRIAL //
14 DAY TRIAL //