Security researchers have come across a Windows Trojan, Trojan.Droidpak, that’s designed to infect the Android devices connected to the affected computer.
When it infects a computer, the threat drops a malicious DLL file and registers it as system service. After that, it downloads a configuration file, which is parsed in order to retrieve a malicious APK file, Symantec experts explained in a blog post.
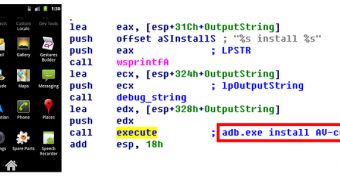
In the next phase of the attack, the Android Debug Bridge Tool is installed. The application is utilized to install the malicious APK onto the Android devices connected to the infected computer.
To make sure that the infection is successful, the process is repeated a number of times. However, it only works if the USB debugging mode is enabled on the Android smartphone.
Once it’s installed, the Android threat poses as a Google App Store program. The malware, Android.Fakebank.B, is actually a malicious replica of a Korean online banking application.
If the legitimate banking app is detected on the infected device, it’s removed and replaced with the fake one. The malware is also capable of intercepting SMS messages and sending them to cybercriminals.
 14 DAY TRIAL //
14 DAY TRIAL //