When it launched Windows Vista back in January 2007, Microsoft made sure to emphasize added security as part of the Wow. The company has yet to unveil its marketing strategy for Windows 7, although the evolution of user protection is bound to be a strong selling point, but the operating system has already passed an important test in terms of security. The 15 Windows vulnerabilities plugged in the latest release of Microsoft security bulletin on August 11, 2009, have left Windows 7 RTM without a scar. Well, almost. The software giant did release one patch for Vista's successor. Definitely without a scar. The patch released is for Windows 7 Release Candidate Build 7100 and not for the RTM Build.
Security Update for Windows 7 (KB973540) and Security Update for Windows 7 for x64-based Systems (KB973540) are currently available for download from Microsoft, and are designed to patch the Critical Microsoft Active Template Library (ATL) vulnerabilities resolved with Microsoft Security Bulletin MS09-037. This despite the fact that under the Non-Affected Software section Microsoft enumerates the following platforms: Windows 7 for 32-bit Systems, Windows 7 for x64-based Systems, Windows Server 2008 R2 for x64-based Systems and Windows Server 2008 R2 for Itanium-based Systems.
UPDATE: I received additional information from Microsoft on this specific matter. , Windows 7 RTM is in no way affected by any of the security vulnerabilities addressed by MS09-037, a Microsoft spokesperson told Softpedia. “However, the vulnerable code does exist in Windows 7 Release Candidate (RC) 1, which is still supported by Microsoft. Microsoft has released an update for Windows 7 RC1 as a result,” he added.
“As part of Microsoft’s commitment to deliver security updates on a predictable and consistent monthly schedule, Microsoft released nine security bulletins to help protect customers from 19 vulnerabilities in Windows, the .NET Framework, Microsoft Office, Microsoft Visual Studio, Microsoft ISA Server, Microsoft BizTalk Server and Remote Desktop Client for Mac,” revealed Christopher Budd, security response communications lead for Microsoft.
The specific vulnerabilities in Microsoft Active Template Library that are resolved by the Windows 7 patch can potentially allow an attacker to perform remote code execution if an exploit attempt is successful. Microsoft informs that attacks would need to trick victims into loading malformed components or controls served through malicious websites.
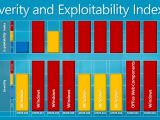
“This month, we released nine security bulletins. Five of those are rated Critical and four have an aggregate severity rating of Important. Of the nine updates, eight affect Windows and the last one affects Office Web Components (OWC). It is also important to note that five of the six critical updates also have an Exploitability Index rating of “1” which means that we could expect there to be consistent, reliable code in the wild seeking to exploit one or more of these vulnerabilities within the first 30 days from release. The chart below shows the aggregate severity summary and exploitability index ratings for all nine bulletins. This overview chart should guide you in prioritizing this month’s updates in order to protect your systems efficiently and effectively,” stated Jerry Bryant, senior security program manager lead.
Below you will be able to find a list with all the security bulletins released by Microsoft on August 11, courtesy of Christopher Budd:
- MS09-036 (Maximum severity of Important): This update resolves a privately reported vulnerability in the Microsoft .NET Framework component of Microsoft Windows, which could allow a denial of service attack. This update received a 3 rating from Microsoft’s Exploitability Index.
- MS09-037 (Maximum severity of Critical): This update resolves five privately reported vulnerabilities in Microsoft Active Template Library (ATL), which could allow remote code execution. This update received a 1 rating from Microsoft’s Exploitability Index.
- MS09-038 (Maximum severity of Critical): This update resolves two privately reported vulnerabilities in Windows Media file processing, which could allow remote code execution. This update received a 2 rating from Microsoft’s Exploitability Index.
- MS09-039 (Maximum severity of Critical): This update resolves two privately reported vulnerabilities in the Windows Internet Name Service (WINS), which could allow remote code execution. This update received a 1 rating from Microsoft’s Exploitability Index.
- MS09-040 (Maximum severity of Important): This update resolves a privately reported vulnerability in the Windows Message Queuing Service (MSMQ), which could allow elevation of privilege. This update received a 1 rating from Microsoft’s Exploitability Index. - MS09-041 (Maximum severity of Important): This update resolves a privately reported vulnerability in the Windows Workstation Service, which could allow elevation of privilege. This update received a 1 rating from Microsoft’s Exploitability Index. - MS09-042 (Maximum severity of Important): This update resolves a publicly disclosed vulnerability in the Microsoft Telnet service, which could allow an attacker to obtain credentials. This update received a 1 rating from Microsoft’s Exploitability Index.
- MS09-043 (Maximum severity of Critical): This update resolves four privately reported vulnerabilities in Microsoft Office Web Components, which could allow remote code execution. This update received a 1 rating from Microsoft’s Exploitability Index.
- MS09-044 (Maximum severity of Critical): This update resolves two privately reported vulnerabilities in Microsoft Remote Desktop Connection, which could allow remote code execution. This update received a 1 rating from Microsoft’s Exploitability Index.
- Microsoft released Security Advisory (973811) to include a non-security update that enables new protection technology on the Windows platform that can be used by both third-party applications and Microsoft software to enhance the protection and handling of credentials when authenticating network connections using Integrated Windows Authentication (IWA).

 14 DAY TRIAL //
14 DAY TRIAL //