With the latest move on the evolution from Beta to Release Candidate Microsoft is proving that it's not all about adding features when it comes to advancing the development process of Windows 7. Applying “the end justifies the means” tactic Microsoft has amputated the AutoPlay/AutoRun feature from the upcoming Windows 7 Release Candidate development milestone, arguing a stringent need to counter malicious code behavior and increase the security of Windows users. For the time being only Windows 7 will feature the AutoPlay changes in relation to USB devices, but the Redmond company plans to extend the security mitigation to Windows Vista and Windows XP.
“Windows will no longer display the AutoRun task in the AutoPlay dialog for devices that are not removable optical media (CD/DVD.) because there is no way to identify the origin of these entries. Was it put there by the IHV, a person, or a piece of malware? Removing this AutoRun task will block the current propagation method abused by malware and help customers stay protected. People will still be able to access all of the other AutoPlay tasks that are installed on their computer,” explained Arik Cohen, a program manager on the Core User Experience team.
Jimmy Kuo and Huzefa Mogri from the Microsoft Malware Protection Center explained that Microsoft had come to detect on average at least a quarter of a million malware samples that made use of the AutoPlay functionality in order to spread through USB devices. Such malicious software is capable of altering or writing a malformed autorun.inf file on the USB in order to trick victims into executing malware instead of performing mundane tasks such as viewing the contents of removable media.
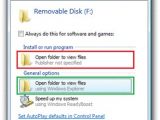
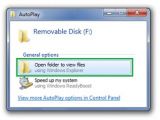
The Conficker worm is the most recent example of malware that has leveraged AutoRun as an infection vector. An infected USB device displays two “Open folder to view files” options in the AutoPlay dialog box, just as in the screenshot on the left. Still, the first, residing under the Install or run program, actually executes Conficker, and does not allow the users to view the contents of the USB. This issue was reported even in Windows 7 Beta back in January 2009. Starting with Windows 7, the AutoRun functionality will be blocked entirely for USB devices. End users will only get the General options when inserting a USB drive, with tasks provided by the Windows operating system.
“CDs and DVDs (including CD emulation), where the IHV specified AutoRun task authored during manufacturing, will continue to provide the AutoRun choice allowing customers to run the specified software,” Cohen added. “IHVs of generic mass storage devices should expect that people will browse the contents of the device to launch any software. The new behavior will allow customers to continue to use AutoPlay (including all Windows and ISV installed tasks) to access their media and devices while not being presented with tasks from malware. Additionally, device classes, such as portable media players and cell phones, now support Device Stage on Windows 7. Device Stage offers the IHV a multifunction alternative to AutoPlay where they can present links to software and common tasks, and provides additional features as you use the device.”

 14 DAY TRIAL //
14 DAY TRIAL //