Windows 7 is almost immune to a piece of malware that has proven a real nightmare to users running older versions of the Windows client. Windows XP SP3 customers particularly have been hit extremely hard by Alureon, a rootkit that failed to play nice with a Windows kernel update and ended up rendering unbootable infected PCs earlier this year. Microsoft’s Malicious Software Removal Tool cleaned no less than 356,959 Windows computers infected with Alureon, with the Redmond company pointing out that the statistics are associated exclusively with the May release of MSRT. Out of all the machines cleaned by the software giant’s free security tool, only 3.5% were running Windows 7.
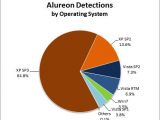
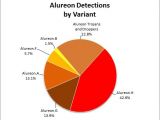
In this context, Alureon comes to prove just how unsafe are older versions of Windows, as XP SP3 PCs account for the bulk of infections, no less than 64.8%. The runner-up is XP SP2 with 13.6%, Vista SP2 with 7.3%, Vista RTM with 6.9% and Vista SP2 with 3.8%. Combined, machines running XP SP2 and SP3 make up 78.4% of all the Windows computers compromised by the rootkit. At this point in time, Virus:Win32/Alureon.H is the most prevalent flavor of the browser, having been cleaned from 155,394 PCs, Vishal Kapoor and Joe Johnson, from the Microsoft Malware Protection Center, note.
“The new .H variant is the most prominent in terms of prevalence. There were several changes to the design of the rootkit to avoid detection and cleaning, revealing that the rootkit is still under active development and distribution. One of the notable changes was to infect arbitrary system drivers instead of only the hooked miniport driver. Expectedly, this can have negative side effects on the machine depending on the chosen driver. For example, we’ve seen some machines having their keyboard disabled as a result of an infection. On other machines, Windows XP unexpectedly requests reactivation because the infection appears like a significant hardware change,” Johnson reveals.
The Redmond company indicates that the authors of Alureon are working to upgrade older versions of the rootkit to the most recent builds, which are better equipped to dodge antivirus products. The April version of the MSRT cleaned Alureon from 262,969 machines, namely 37% less compared with May. As far as the MSRT May malware families go, Alureon has climbed to the first spot, the software giant notes.
“Continuing the trend from last month, more than three-quarters of the infections occur on machines running Windows XP. This is likely due to better security in the later versions of the Microsoft Windows operating systems. The dominance of XP SP3 can be attributed to the combination of the above in conjunction with its high prevalence of use,” Johnson adds.
Microsoft’s Malicious Software Removal Tool is available for download here.

 14 DAY TRIAL //
14 DAY TRIAL //