Security researchers have come across a spam campaign that’s designed to distribute malicious elements on Java, Android, and iOS mobile devices.
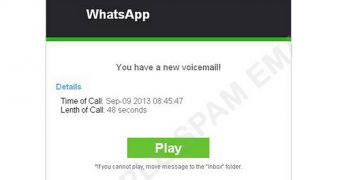
The attack starts with a fake WhatsApp email that informs recipients of a new voicemail. When the Play button from the email is clicked, depending on their device, users are taken to a malicious website.
PC users are taken to a site that instructs them to update their browser. The browser update is actually a .jar file (browser_update_installer.jar). This malicious Java file appears to be designed for users who access the emails from their Java phones.
In case the fake WhatsApp notification is accessed from an Android device, the victim is presented with an .apk browser update file. The threat is detected by Trend Micro as ANDROIDOS_OPFAKE.CTD.
If it’s installed, the malware starts sending out text messages to specific phone numbers. In addition, it attempts to convince the victim to download another app.
In the case of iOS users, they’re presented with a download progress bar after they click on the link. However, the operating system’s restrictions block the app from being installed.
However, experts warn that the malicious application might pose a risk to users with jailbroken devices.
 14 DAY TRIAL //
14 DAY TRIAL //