Websites displaying seals of trust issued by third-party site security entities are not necessarily risk-free, despite the scanning of the code in search of vulnerabilities that can be exploited, a research paper reveals.
The study shows that the security logo from popular seal providers is not to be taken for granted because the automated scanning performed by the entities is limited, and an attacker with limited resources could find a weakness to exploit within a working day.
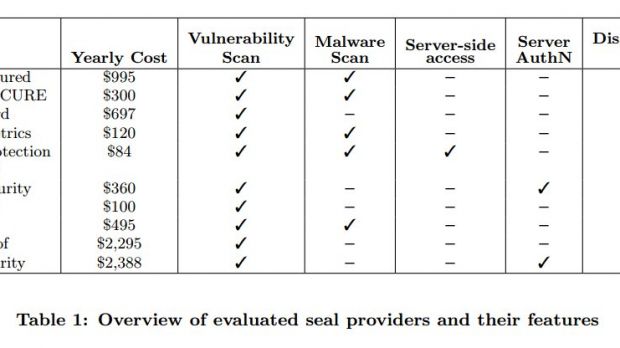
In the experiment, researchers from Stony Brook University and the University of Leuven chose websites with the security seal of approval from ten popular providers, Symantec and McAfee among them.
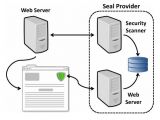
A security seal is intended to attest that a certain website does not present a risk to the shopper as a result of a security scanning routine that can sometimes occur even on a daily basis.
Generally, the verification refers to vulnerabilities that could be exploited, but multiple services can also scan for the presence of malware. If a security risk is detected, the website administrators are provided with details about the issue and where it resides, as well as with indications about correcting the problem.
Certified sites fall during manual pentesting session
The researchers found that the vulnerability scanning was not as effective as one might think because the check was done against a list of automated attacks; on the same note, they said that the best scanner managed to detect less than half of the known vulnerabilities.
As a demonstration, they conducted manual penetration tests on a number of nine certified websites and discovered high-risk weaknesses in less than eight hours, proving that moderately motivated attackers could break in and access sensitive information.
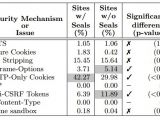
Despite looking for thousands of vulnerabilities, the scanners missed some of the most common ones, like SQL injection, cross-site scripting (XSS) and CSRF (cross-site request forgery).
“In our manual analysis, we could register on the websites under evaluation, access content that requires authentication, and reason about prices in shopping carts – actions that are not supported by the automated scanners of most seal providers,” the researchers wrote in a paper called “Clubbing Seals: Exploring the Ecosystem of Third-party Security Seals.”
These are the results of multiple actions that cannot be replicated through automated scanning. Additionally, the automated tools missed XSS flaws where GET and POST parameters were reflected without proper encoding.
Scanners miss known glitches
Another stage of the experiment included building a shopping website that relied on a version of a shopping cart software known to be vulnerable to a certain XSS glitch. The site was also “enriched” with other vulnerabilities, amounting to a total of 12.
Only eight seal providers could be tested in this attempt, because two of them requested proof of a real business in order to unlock the trial.
The results showed that no service could find more than five of the holes planted by the researchers, although most of them were well-known ones.
Trust labels can enable cybercriminals to find vulnerabilities
It appears that the trust label from the security companies could serve threat actors to identify vulnerable targets and the exact glitch that can be exploited.
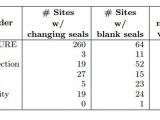
Attackers can determine whether a website is vulnerable or not just looking at the seal of trust displayed. Most of the times, the seal changes its state when an issue is detected; the date of the last scan is also an indicator of the security status.
According to the researchers, a malicious actor could send out crawlers looking for a change in the seal state on a daily basis. This method does not work for all providers of trust labels, though.
To determine the type of vulnerability plaguing the targeted website, the attackers can resort to the services of the seal provider for a site of their own, either purchasing it or using a free trial, and find the requests made during a scan (files, a parameter reflected without encoding, execution of an SQL statement). Collecting these requests and replaying them against the target could lead to the discovery of the vulnerability.
Phishing websites with a trust seal increase confidence
Holiday shoppers should pay particular attention to the websites they buy from, even if there is a seal of trust displayed, and try to rely as much as possible on services from reputable brands, which are more likely to revise the security state of their websites.
Another threat buyers have to keep away from are phishing websites that could feature the seal of confidence, the researchers say.
In a different experiment, they found that a seal of trust could be obtained for a fraudulent website if the referrer header of an HTTP request were absent, something that is trivial to achieve. This would make the fake website look legit, since it does bear a valid mark of trust.

 14 DAY TRIAL //
14 DAY TRIAL //