Last week, expert from Solutionary provided an interesting graph regarding the evolution of Java vulnerabilities since 1996 and until present day.
On Monday, Websense published a report which showed that over 93% of endpoints used an unpatched variant of Java that could be exploited by cybercriminals with the Cool exploit kit.
The report is based on data collected from tens of millions of endpoints by the company’s Advanced Classification Engine (ACE). To get a real-time telemetry about vulnerable Java versions, the data has been pumped into the Websense ThreatSeeker Network.
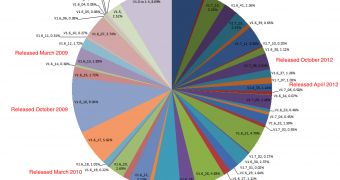
According to the security firm, only around 5% of web browser users utilize the latest Java Runtime Environment, which is JRE 7 update 17.
Even more worrying is the fact that many users (78.86%) still haven’t migrated to Java 7, which means that their systems are highly vulnerable to cyberattacks.
“Grabbing a copy of the latest version of Cool and using a pre-packaged exploit is a pretty low bar to go after such a large population of vulnerable browsers,” Charles Renert, VP of Websense Security Labs, explained in a blog post.
“Most browsers are vulnerable to a much broader array of well-known Java holes, with over 75% using versions that are at least six months old, nearly two-thirds being more than a year out of date, and more than 50% of browsers are greater than two years behind the times with respect to Java vulnerabilities.”
Besides the exploit for Java 7 update 15, which affects 93% of the population of browsers, Cool also contains exploits for Java 7 update 11 and Java 7 update 7, to which 84%, respectively 74% of endpoints are vulnerable.
Exploits for Java 7 update 6 and update 4 are integrated into Blackhole 2.0, RedKit, CritXPack or Gong Da. Nearly three quarters of the endpoints analyzed by Websense could be compromised by these exploits kits.
 14 DAY TRIAL //
14 DAY TRIAL //