Vulnerability Lab researchers have found that a medium severity software filter security hole in KeePass Password Safe could be leveraged by a cybercriminal to manipulate context, launch phishing attacks and even steal plain text password lists.
The issue affects the 1.22 and all the older versions of the popular open source password manager. Fortunately, the experts collaborated with Domenic Reichl, the developer of the application, and the vulnerability will be addressed with the release of the 1.23 variant.
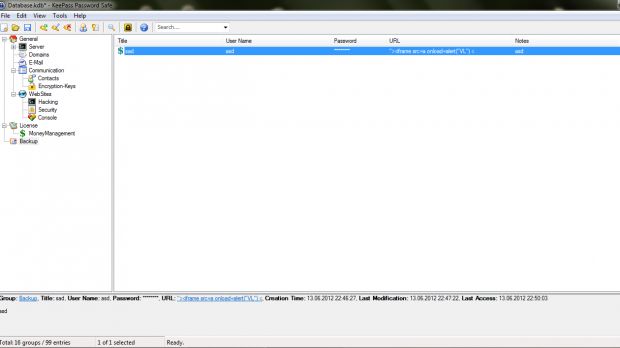
The bug, located in the filter/validation module of the import/export section, allows an attacker to inject malicious code during the exportation of a database.
“Exploitation of the vulnerability requires a manipulated URL with malicious script code, a logging server with chmod 777, a listing file (random) & a KeePass v1.22 user,” experts explained.
“The bug will be injected on the remote way, affects the local validation (html/xml) and change the technic back when remotely transferring the password lists. The injection of the malicious URL/domain context can be done via auto save of URLs (victim) or manually (reproduce).”
An attacker with local access can manipulate the database and execute persistent script code (html/js) within the clean HTML template generated by KeePass Password Manager.
Vulnerability Lab has provided a detailed exploitation scenario which requires only a medium level of user interaction.
First, the attacker sends the victim a specially crafted login page that contains a piece of code in the URL’s parameters. This script calls an HTML or a JavaScript which executes a chmod 777 command that gives full permissions to a file when processing local requests.
The victim saves the URL via the “auto type engine” module of the application, and later, when he/she wants to export the file as a plain HTML, the malicious script grabs its contents and sends it back to the attacker.
When the new variant of KeePass Password Safe is released, it will be available for download here. In the meantime, beware of suspicious links that may be sent by cybercriminals who are after your list of passwords.
 14 DAY TRIAL //
14 DAY TRIAL //