A flaw in the manifest file for Android apps can be exploited to trigger memory exhaust by the Package Parser and cause a denial of service (DoS) condition on the device.
The glitch persists even after the phone has been restarted, thus sending it into a reboot loop. According to security researchers, removing the buggy app causing the trouble is not possible and the reboots continue until the battery is completely drained.
Package parser depletes memory resource
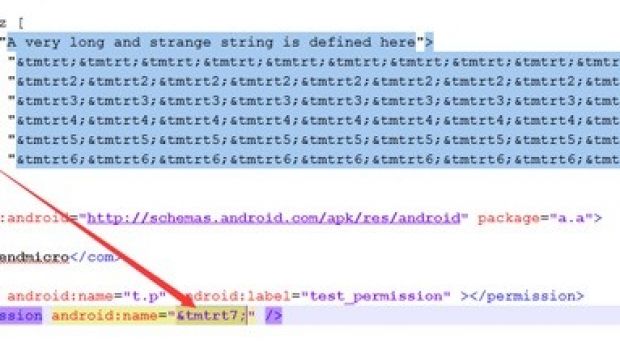
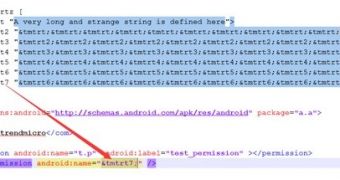
The manifest file for Android apps is in XML format, whose structure is defined using a document type definition (DTD) declaration.
It appears that the DoS condition occurs in the case of apps that include a reference to a huge string in the manifest. This can be achieved by assigning the reference to different tags, such as permission name.
The Package Parser would then need more resources to go through the entire string, and if more memory is needed than it is available, the consequence is a crash of the parser. A chain reaction is initiated by this, including stopping all running services, thus forcing the device to reboot.
Researchers at Trend Micro discovered the glitch and witnessed its effect on multiple versions of Android, including KitKat and LolliPop.
Removing the reboot cause is not too easy
Considering that the culprit app cannot be eliminated because the device is restarting continuously, the only option is to flash the ROM or to re-install the operating system, researchers say.
Either of these operations requires some technical knowledge, as it involves working with Android Debug Bridge (ADB) tool and leads to removing the data stored on the device, unless there is support for a removable memory card.
Booting into recovery mode and resetting the device to its factory defaults should also do the trick.
The researchers said that they managed to reach the same DoS result through another method, which involves using an intent-filter that is also included in the manifest file.
“An icon will be created in the launcher if the manifest file contains an activity definition with this specific intent-filter. If there are many activities defined with this intent-filter, the same number of icons will be created in the home page after installation. However, if this number is too large, the .APK file will trigger a loop of rebooting,” said Simon Huang, mobile security engineer at Trend Micro.
The potential risk incurred by the user is data loss, if a backup is not available. There is no financial gain involved with an attack leveraging an Android app with a malformed manifest file, but pranksters could upload them to third-party marketplaces just to have a few laughs.
 14 DAY TRIAL //
14 DAY TRIAL //