It appears that the consistent efforts that Microsoft has poured into Windows Vista via the Secure Development Lifecycle are really paying off. In this context, the Redmond company's claim that Vista is the most secure Windows operating system on the market accurately reflects the superiority of Microsoft's latest platform. Illustrative in this sense is a new example of a zero-day vulnerability impacting Windows XP and Windows Server 2003.
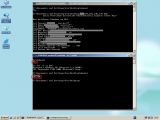
Elia Florio, Symantec Security Response Engineer, revealed that a successful exploit leads to local privilege escalation, but at this point, the security flaw was confirmed only on fully patched Windows XP SP2 and Windows Server 2003 SP1, but not on Windows Vista. Essentially, a user with local access to an XP or 2003 machine can gain higher privileges on system shell from a restricted account.
"At this time, we will not disclose the details of the vulnerability; however, we'll just say that the affected component is a driver that is shipped in many Windows installations by default. It is also included in the i386 folder. Under some circumstances, this driver can write into the kernel memory without proper restrictions", Florio explained.
The main mitigating factor is the fact that the vulnerability is not remotely executable. A potential attacker would have to have physical access to the computer in order to run the exploit. Florio confirmed that Microsoft is already aware of the flaw, and that a patch is cooking.
"At the moment, it's still not clear how the driver is used by Windows because this file does not have the typical Microsoft file properties present in other Windows system files. Since this exploit was used in the wild, we are recommending system administrators be extremely careful at this time and restrict or disable access to unnecessary services for all accounts except for administrator-level users", Florio added.

 14 DAY TRIAL //
14 DAY TRIAL //