Even before the release of Windows 7 Release Candidate Build 7100 Microsoft announced that it would take extreme measures in order to increase end user protection and amputate the AutoPlay/AutoRun feature of the operating system. Over a months after Windows 7 has been released to manufacturing, Microsoft is applying the same security strategy to previous Windows releases. The Redmond company is making sure that the amputated AutoPlay/AutoRun in Windows 7 will make its way to Windows XP (including SP3), Windows Server 2003, Windows Vista (including SP2), and Windows Server 2008, for security reasons.
In this regard, Microsoft has already made available an update designed to limit the AutoPlay/AutoRun functionality in Windows 7’s precursors. Essentially, following the implementation of the refresh, the AutoPlay/AutoRun will no longer display the “Install or run program” option for USB drives.
“In Windows XP, Windows Vista, and Windows Server 2003, AutoRun entries were populated for all devices that had mass storage and had a validly formatted AutoRun.inf file in the root directory. This included CDs, DVDs, USB thumb drives, external hard disks, and any volume that exposed itself as mass storage. This update disables AutoRun entries in AutoPlay, and displays only entries that are populated from CD and DVD drives. Effectively, this prevents AutoPlay from working with USB media,” Microsoft explained.
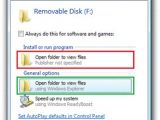
Back at the start of 2009 the Conficker worm was making a rampage, spreading at a fast pace, and having already infected millions of computers. One of the preferred methods of self-spreading for the worm was to infect removable devices, including USB drives. When a compromised USB drive was inserted into a new machine, a malformed variant of the AutoPlay/AutoRun dialog box would pop up. In this case, the end users were presented with two “Open folder to view files” options that appeared similar. However they were anything but that.
As you can see from the screenshot on the left, only the bottom “Open folder to view files” option actually opens up the contents of the USB and allows access. Clicking on the first “Open folder to view files” option would instead “install and run program” namely the virus that had infected the USB, also compromising the computer.
“Users who install this update will no longer receive a setup message that prompts them to install programs that are delivered by USB flash drives. Users will have to manually install the software. To do this, users click Open folder to view the files, browse to the software's Setup program, and then double-click the Setup program to run the program manually,” the company added. “Some USB flash drives have firmware that present these USB flash drives as CD drives when you insert them into computers. These USB flash drives are not affected by this update.”
- Update for Windows Server 2008 (KB971029) - Update for Windows Server 2008 for Itanium-based Systems (KB971029) - Update for Windows Server 2008 x64 Edition (KB971029) - Update for Windows Vista (KB971029) - Update for Windows Vista for x64-based Systems (KB971029) - Update for Windows Server 2003 x64 Edition (KB971029) - Update for Windows Server 2003 for Itanium-based Systems (KB971029) - Update for Windows Server 2003 (KB971029) - Update for Windows XP (KB971029)

 14 DAY TRIAL //
14 DAY TRIAL //