Google’s malware scanning service VirusTotal can be employed to find clues about the identity of malware creators that test their viruses before deploying them in the wild.
A security researcher (@9bplus) spent about five years monitoring the behavior of certain uploaders, gleaning information from the submitted data in order to connect them to threat actors and to identify targeted victims.
In the research, he used the paid variant of the service, which offers more information through search functions and metadata collected from the users.
Judging by the data uploaded to the service, multiple categories of user accounts can be detected: antivirus companies, targets, threat actors, and a general class, which includes “users that appear to be associated in a number of categories, but mostly upload benign information or files with a high number of associated submitters.”
Discerning between the classes is done by analyzing the frequency and amount of data verified through the service and the metadata associated with it.
“During the research, two methods were discovered to track and identify likely actor activity within Virustotal,” @9bplus writes in a paper hosted in Google cloud. These are the uploader behavior and unique file fixation.
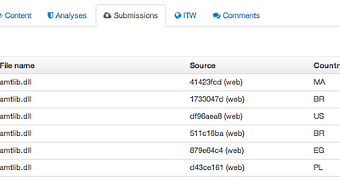
Both of them have in common the fact that the same filename pattern is used, which can indicate a threat actor that tests incremental versions of malware.
The system created by the researcher relies on assigning scores for the particularities of the submissions from a certain account, such as uploading data within short periods of time, verifying duplicates, checking files with a pattern-based name or those with a re-used filename pattern.
“This score value can then be used in conjunction with other features such as total number of uploads, country of origin and so on to improve the filtering of suspicious accounts. If implemented properly, it’s possible to automate the discovery of likely actor activity for an analyst to review,” says the researcher.
Based on this system, @9bplus was able to identify several accounts belonging to actors testing and distributing advanced persistent threats (APTs). He observed the activity of one group, which started with a single account and then created more than 15, used for uploading over 100 samples.
During the time (mid-August – November, 2012) they used the service to improve the malicious file, and they adopted measures to prevent the leak of details about their infrastructure before deploying the malicious operation.
In another example, bad actors testing NetTraveler displayed behavior similar to that of a target, but the filename patterns and the files themselves led to labeling them as the authors of the malware.
 14 DAY TRIAL //
14 DAY TRIAL //