Google’s malware-scanning service VirusTotal has just been improved. Starting today, besides .exe, .pdf and .apk files, information security researchers and security enthusiasts can also analyze .pcap (packet capture) files.
PCAP files are utilized for packet sniffing and analyzing data network characteristics.
They’re often used in the malware research field to record honeyclient browser exploitation traces, log network activity seen by appliances, and record malware communications when executed in a sandbox.
“We have seen that many users send their PCAPs to VirusTotal, these PCAPs often contain HTTP flows whereby a trojan is downloaded, recording worm scanning sweeps, logging exploits being delivered to a honeymonkey, etc. We want to help those users submitting PCAPs to VirusTotal and improve their research,” VirusTotal’s Emiliano Martinez wrote in a blog post.
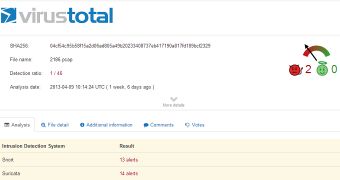
The PCAP analysis feature introduced by VirusTotal is capable of listing the performed DNS resolutions, listing HTTP communication, extracting file metadata with Wireshark, and processing the files with popular intrusion detection systems.
Here is an example of a PCAP file scan.
 14 DAY TRIAL //
14 DAY TRIAL //