An ongoing malicious campaign delivering Vawtrak banking Trojan has been identified by security researchers to target customers of multiple banks in Canada.
The malware is also known by the names Neverquest and Snifula, and it is an advanced piece capable of stealing financial information and executing transactions from the compromised computer through remote desktop control, thus hiding its tracks.
Its authors rely on real-time web injection tactics to present the victim with fraudulent screens asking for the information necessary for accessing their online banking account.
This method is also used for harvesting two-factor authentication (2FA) codes that are generated by separate tokens, usually based on offline card verification or its PIN number.
C&C servers were registered in February
Security researchers at Heimdal Security analyzed the methods used by the cybercriminals to distribute Vawtrak and determined that it spread via drive-by download attacks, phishing campaigns on social media websites, as well as spam.
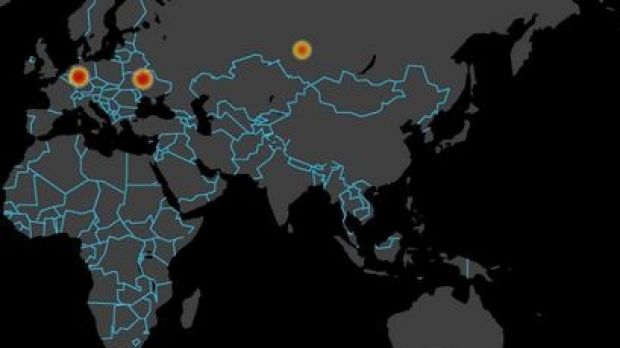
They say that the variant analyzed by them targets more than 15 financial institutions from Canada and it connects to six command and control (C&C) servers in different parts of the world.
Running a whois search on them, we learned that all but one were registered on February 25, 2015.
The last one appears to have been registered on February 16, 2015, which could also be an approximate date of the beginning of the malicious campaign.
In an in-depth analysis conducted by researchers from antivirus company AVG, Vawtrak is presented with a complex set of features that includes protection against a large number of security solutions that may be running on the infected computer.
The malware tries to disable the antivirus products by enabling the Software Restriction Policies mechanism available on Windows systems. The feature is intended for network administrators, offering them control over the software executed on controlled endpoints.
Vawtrak gets stronger, it is not going anywhere
Additional functionality present in the latest versions of Vawtrak refers to stealing sensitive information such as passwords from different programs (via Pony infostealer module), digital certificates and cookies, logging keystrokes and capturing video and screen images.
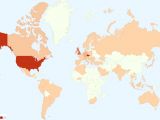
AVG says that the malware is not showing any signs of decreased activity and that minor changes in its features, targeted regions and banks create detection spikes every two to five days.
Based on their telemetry data, the countries most affected by this threat are the Czech Republic, USA, UK, and Germany.
The conclusion reached by AVG following their analysis of the malware is that “Vawtrak is like a Swiss Army knife for its operators because of its wide range of applications and available features.”
 14 DAY TRIAL //
14 DAY TRIAL //