Security researcher Behrouz Sadeghipour has uncovered several vulnerabilities in Yahoo Taiwan’s Fashion subdomain. The list of security holes includes authentication bypass, and full path and MySQL credentials disclosure.
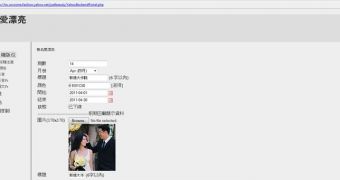
First, the expert uncovered a login page for the Fashion section of the website. However, he managed to bypass the authentication, which enabled him to add new content, edit content and even upload files.
Sadeghipour has also found a full path disclosure flaw and has even gained access to MySQL credentials “by messing around” with POST requests. The expert also believes that there might have been an SQL injection vulnerability in the administration panel, but Yahoo fixed the issues before he could test this theory.
Yahoo has quickly patched the vulnerabilities, but the company has informed the researcher that the flaws are out-of-scope for the bug bounty program.
This isn’t the first time Sadeghipour reports security holes to Yahoo. In March, he identified a remote code execution vulnerability in Yahoo’s Hong Kong subdomain. In April, on the same subdomain, he discovered a total of 8 files vulnerable to SQL Injection attacks.
For additional details on the latest Yahoo vulnerabilities reported by the expert, check out his blog. You can also take a look at the video proof-of-concept published by the researcher:
 14 DAY TRIAL //
14 DAY TRIAL // 