A fresh sample of the Upatre malware downloader is currently distributed via emails claiming to be from different banks.
The messages come with a link purporting to point to a document from the financial institution but which leads to a version of the Upatre malware, used by cybercriminals to funnel in threats with specific purposes.
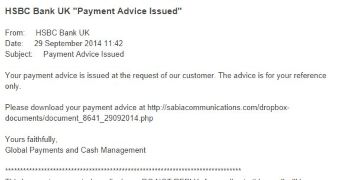
The campaign spreads emails with a different message in the body, but they all lead to the same file, posing as a bank account document or payment advice information.
Conrad Longmore at Dynamoo’s blog caught two such samples, one of them impersonating communication from Lloyds Commercial Bank, and the other claiming to be from the HSBC bank in UK.
In both cases, a link is provided to download file “document_8641_29092014_pdf.scr,” which is an executable that plants Upatre on the system.
A first analysis on VirusTotal showed that the malware variant had low detection among the antivirus engines available on the service, being identified as a threat by only one solution. Detection is increased at the moment, 16 out of the 55 scan engines labeling the file as malicious.
Details about the file show that it includes a total of five Portuguese PE resources and connects to cuscorock[.]com and formatech[.]es to download an item.
 14 DAY TRIAL //
14 DAY TRIAL //