Georgian security researcher Ucha Gobejishvili has identified a memory corruption vulnerability in Firefox 13, the latest variant of Mozilla’s popular web browser.
To demonstrate his findings, the expert has made available a working proof-of-concept, along with a video to show how it works.
Gobejishvili told Softpedia that Mozilla confirmed the existence of the vulnerability and planned on fixing it in the upcoming versions.
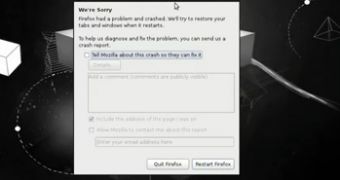
In the video, the researcher showed that by launching the specially crafted HTML file the vulnerability would be triggered, causing a denial-of-service (DOS) state.
In practice, an attacker would have to host a website that contains the malicious webpage. Then, with the aid of cleverly designed emails or instant messages, he could lure potential victims to the website.
As many of our readers probably know, this is a basic task for most cybercriminals. Simply forge an email to make it look like it comes from a renowned company, carefully place a couple of warning messages, and salt it with some links that point to the website. Presto, you have a malicious campaign.
Regarding Firefox, Mozilla has already presented a few improvements in the security department with the release of the 14 Beta variant of the web browser. The most important of them is the introduction of HTTPS connections by default for Google searches.
In unrelated news, Ucha Gobejishvili was one of the experts that helped us create a comprehensive password security advisory from which users can learn not only how to choose strong passwords, but also how to store them safely.
The article features recommendations from famous professionals such as Graham Cluley of Sophos, David Barclay from Trend Micro, Avira’s Sorin Mustaca, and others.
Here is the denial-of-service proof-of-concept made available by the researcher:
 14 DAY TRIAL //
14 DAY TRIAL // 