A new spear-phishing campaign has been detected to deliver a fresh version of NetTraveler malware, which features an encrypted configuration file.
The malware, also known as “Travnet” and “Netfile,” has been active for as long as ten years, as researchers at Kaspersky found clues indicating that its activity began in 2004; for the entire duration of monitoring, the researchers noticed that its primary targets were Uyghur and Tibetan activists. The profile of the victim has not changed for the latest campaign.
Analyzing a sample email delivering NetTraveler, Costin Raiu and Kurt Baumgartner, both security researchers at Kaspersky Labs, said that the computers of the targets were infected via a malicious DOC file.
The document contains an exploit for a vulnerability in Microsoft Word with the identifier CVE-2012-0158. The glitch was reported in October 2012 and has since been patched, but there are many systems with an older version of Word that are vulnerable to this flaw.
It has been used in multiple cyber espionage campaigns, one of the most prominent being Red October.
The researchers observed that the configuration file for the latest revision of the malware was no longer available in plain text; but the authors did not use complex encryption, and the researchers were able to find the command and control (C&C) servers providing instructions.
In the samples analyzed, Kaspersky found C&C servers located mostly in Hong Kong, with only one in seven being based on United States territory, in Los Angeles.
The registrar for the Chinese-based severs is Shanghai Meicheng Technology, while for the one in the US is TodayInc.com.
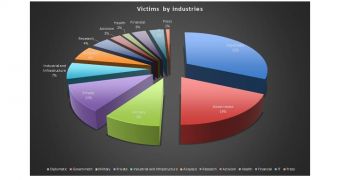
The cyber espionage character of the campaign is obvious, but more evidence that supports this has been discovered, as most of the victims are from the diplomatic and government sector.
“For 10 years NetTraveler has been targeting various sectors, with a focus on diplomatic, government and military targets,” a blog post from Kaspersky says.
32% of the victims are from the diplomatic sector, while 19% of them are linked to the government, according to older telemetry from the security firm.
NetTraveler can exfiltrate data from the affected system such as documents and private information as well as log activity and send it to the commanding server.
In another cyber espionage operation, dubbed Machete, also uncovered by Kaspersky, the threat actors had a similar focus, targeting Spanish-speaking individuals connected to intelligence services, military organizations, embassies and government institutions.
 14 DAY TRIAL //
14 DAY TRIAL //