The Trojan horse that builds Peer-to-Peer botnets has evolved. On Saturday 20, 2007, you have been able to read details about the mass spamming of the Trojan.Peacomm, a Trojan horse that connected the compromised machined into a p2p botnet via the UDP port 4,000.
In the three days that have passes since the initial report, Trojan.Peacomm has evolved. The mass spammed emails have different subject lines, the attachment filenames have been modified, the dropped files have also been altered. The evolved Trojan.Peacomm no longer uses UDP port 4,000 to communicate. Instead, it has switched to UDP port 7,871, a change confirmed by the Symantec Threat Management System.
Additionally, Trojan.Peacomm now has rootkit capabilities. According to Amado Hidalgo, Sr. Security Response Manager Symantec, Trojan.Peacomm's rootkit capabilities have not been implemented correctly, and lack sophistication.
"It is now capable of hiding several files and registry keys by hooking several kernel functions and patching the tcpip.sys system driver to hide its ports from commands, such as netstat -o or netstat -b. However, due to some mistakes in the rootkit code, running netstat -and lets you see ports 7871 or 4000 open and waiting for connections".
"It is also important to note that a personal firewall will also notify you of the process services.exe trying to make connections on these ports. Furthermore, the rootkit service can be stopped by running a simple command: net stop wincom32. All files, registry keys, and ports will appear again," explained Hidalgo.
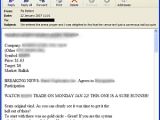
Symantec revealed that the purpose of Trojan.Peacomm is to build a botnet that will be used to send penny stock spam. However, Symantec warned that the botnet's functionality can be adapted to various purposes as it is under the control of the attackers.
"During our tests we saw an infected machine sending a burst of almost 1,800 emails in a five-minute period and then it just stopped. We are speculating that the task of sending the junk email is then passed on to another member of the botnet. My colleagues in the antispam team are seeing greater activity, too," added Hidalgo.

 14 DAY TRIAL //
14 DAY TRIAL //