CVE-2012-1823 is a PHP arbitrary command execution vulnerability uncovered back in May 2012. Despite being discovered and patched a long time ago, cybercriminals have been successfully using it in their operations over the past months.
According to Imperva, an exploit for this vulnerability was made public in October 2013. Variations of the exploit have been used to attack web servers ever since.
The security company has identified as many as 30,000 attack campaigns relying on the PHP exploit in the first three weeks after it was made public. Because many users have failed to update their PHP installations, cybercriminals are still successfully using the exploit.
“We picked up intelligence showing that different botnets have picked up the vulnerability per its effectiveness, and have also captured samples of bot clients that have embedded this vulnerability exploitation in them,” Barry Shteiman, director of security strategy at Imperva, noted in a blog post.
The PHP exploit in question impacts versions 5.4.x and 5.3.x released before 5.4.2 and 5.3.12. 16% of public websites still used these versions and considering that around 82% of all websites use PHP, the potential victims base is huge.
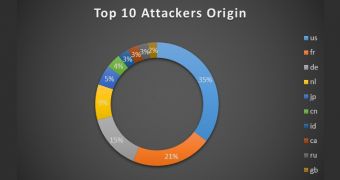
Imperva has set up a honeypot that enabled the company to gather some useful information regarding the attacks. For instance, most of the attacks, 35%, originated from the United States, followed by France (21%) and Germany (15%). Attacks have also been traced back to the Netherlands, Japan, China, Indonesia, Canada, Russia and the UK.
Various URL attack vectors have been used, including //cgi-bin/php, /cgi-bin/php4, /cgi-bin/php.cgi, /cgi-bin/php5, /cgi-bin/php/cgin/php, //cgi-bin/php5, /cgi-bin/php and /cgi-bin/php-cgi. However, the most common one of them, used in over 6,300 attacks, has been //cgi-bin/php.
In terms of volume, the biggest attacks lasted a day or half a day.
“The vast majority of the attackers (86 different attackers IPs) executed their attack in half a day or a one day period attacking a single target. As the attack period and the number of targets grew bigger, the number of attackers dropped significantly,” Shteiman noted in the report.
A total of 43 different types of PHP payloads have been spotted. These payloads are designed to download a malicious executable file from a remote server and run it. Once the malware is executed, it’s removed from the file system. The servers from which the malware is retrieved are usually hijacked machines.
“It is a very intriguing point to show that cybercriminals understand the serious gap that exists between the time that a vulnerability is found in the wild, to the time it gets reported and patched (if third party software/framework is in the loop, such as PHP),” Shteiman explained.
“Finally, there is a time lag until a company becomes aware of both the issues and the fix – and implements it. This creates a window of opportunity for hackers to act on, as they know that the window will be open for a long time.”
Additional technical details on the use of this PHP exploit are available on Imperva’s website.
 14 DAY TRIAL //
14 DAY TRIAL //