The United States Computer Emergency Readiness Team (US-CERT) has issued an advisory to warn users about CryptoLocker ransomware infections.
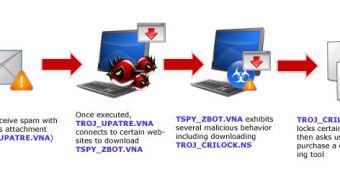
CryptoLocker is a dangerous piece of malware that’s distributed via fake emails that contain malicious attachments. Once it infects a device, the threat encrypts certain files and keeps them that way until a ransom is paid.
“CryptoLocker appears to have been spreading through fake emails designed to mimic the look of legitimate businesses and through phony FedEx and UPS tracking notices. In addition, there have been reports that some victims saw the malware appear following after a previous infection from one of several botnets frequently leveraged in the cyber-criminal underground,” US-CERT noted.
This piece of ransomware is capable of encrypting not only files from the local hard drive, but also ones from USB drives, shared network drives, and external hard drives. It can also access cloud storage drives.
Recently, the cybercriminals behind this threat have launched a decryption service for victims who change their mind about paying up. In case you’ve started cleaning the infection and you realize that there’s no way you can recover the lost files, you can access the service and have the files decrypted.
However, it costs a lot more than paying up right from the start.
Since there’s no way of recovering lost files without paying up, the best thing to do is to take some steps to protect yourself against the threat. The recommendations from US-CERT include performing regular backups; keeping software, including antiviruses, updated; and avoiding suspicious email attachments and links.
You should also make sure firewalls and intrusion prevention systems are properly set up to detect malicious activity, and secure open-share drives to make sure only authorized users can access them.
In case of a CrytoLocker infection, disconnect the impacted machine from the Internet since this might prevent more files from being encrypted. Once the infection is cleaned up, change all your passwords.
Finally, restore the encrypted files from backup, a shadow copy or by performing a system restore.
 14 DAY TRIAL //
14 DAY TRIAL //