A hacker broke into the database of the UK Parliament website by exploiting an SQL injection vulnerability. The incident reveals very poor and questionable password security practices on behalf of the website administration.
The security hole on parliament.uk was discovered by a Romanian greyhat hacker going by the online handle of "Unu," who has made a habit of testing high profile websites for similar bugs. Unu's "hit list" so far includes the websites of large antivirus vendors Kaspersky, BitDefender, F-Secure, Symantec, renowned newspapers, such as The International Herald Tribute and The Telegraph or big ISPs, like British Telecom, Tiscali and Orange France or, more recently, Yahoo! Local.
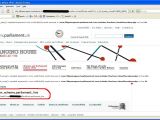
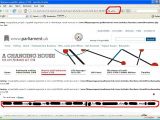
According to Unu, the vulnerability is located in a php script used on the lifepeeragesact.parliament.uk section, which fails to properly sanitize parameters being passed through. This allows a potential attacker to execute SQL queries directly into the database easily by manipulating the URL.
The screen shots published by Unu reveal that the Web server is running on Debian 4.0 (Etch) Linux with a MySQL 5.0.32 database backend. The website's database is called parliament_live; fortunately, it cannot be accessed directly from a remote host.
What is more disconcerting though is what a peak into the database table housing the website's administrative accounts revealed. First of all, the passwords are stored in plain text, which is a major security oversight. Secondly, the passwords are very weak from a security perspective, many being identical to the username they are associated with and almost all of them being common words.
One of the accounts called "fullera" is likely to belong to Alex Fuller, who, according to his LinkedIn profile page, is currently employed as a senior web producer for the UK Parliament. Two other accounts that have captured our attention are called "reida" and "moss," but we are unable to confirm if these belong to Mr. Alan Reid, Liberal Democrat MP, and Mr. Malcolm Moss, Conservative MP.
Unu claimed in the past that he practiced responsible vulnerability disclosure, but just to be on the safe side, we have blotted out any potentially sensitive information from the screen shots below. We have also informed the Webmaster of the UK Parliament website about this vulnerability ourselves.
 14 DAY TRIAL //
14 DAY TRIAL //