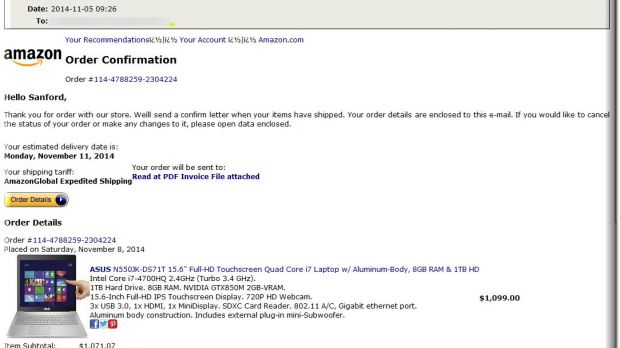
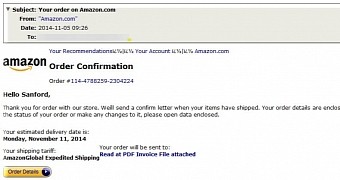
Holiday shoppers at Amazon.co.uk have become a mark for cybercriminals, who started to send large numbers of emails having malicious Microsoft Word documents in the attachment.
The messages try to trick the recipient by purporting to contain information about the shipment of an order. To make the email believable, the subject line includes a number for the alleged package.
Crooks send wave of over 600,000 malicious messages
Researchers at AppRiver, a US-based provider of solutions for protecting against email and web threats, detected the malicious activity on their systems at the end of October and since then, they managed to quarantine a wave larger than 600,000 malicious emails.
Troy Gill, senior security analyst at the company, says that all emails included a Word document embedded with a malicious macro that launches commands for funneling a Trojan dropper on the recipient’s computer system.
The malware type is a keylogger that collects login information for banking accounts, web-based email services and for accessing social media profiles. However, the cybercriminals could switch to a different threat in the future.
A macro is a piece of VBA code that can be integrated in Office to help users automate repetitive tasks; but cybercriminals abuse this feature and include commands for downloading malware.
Microsoft understands the risks associated with macros and has them disabled by default in Office components.
If users do not turn on support for macros, the commands cannot be executed and the risk of compromising the computer is avoided.
More than one cybercriminal group run the scam
According to Gill, another group is currently trying out Amazon customers, this time of the US website. The company caught a total of 160,000 malicious messages in this case.
Some differences can be noted in the body of the email, subject line and method of infection, but the end goal is the same: installing malware.
The message is more believable due to inserting official Amazon graphics, while the lure in the subject line is an order confirmation message.
“Instead of a malicious attachment, these messages utilize links to compromised wordpress sites. Clicking these links will launch the download of a .scr file named: invoice1104.pdf[dot]scr,” says Gill in a blog post; the executable is also a Trojan dropper with the same functionality of adding and installing malware on the computer.
The fact that the downloaded file has the SCR extension instead of that of a regular document (Word, PDF) should ring the alarm bells of the recipient and prevent them from launching it.
The shopping season is when cybercriminal activity reaches its height in a year. Messages related to purchases become a regular thing and the crooks know this all too well. Users are advised to exercise care and pay attention to the content of the message, as well as the links they include and the attachments available.
 14 DAY TRIAL //
14 DAY TRIAL //