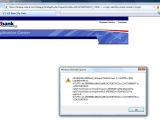
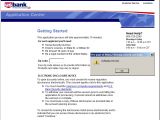
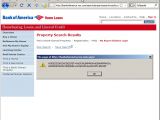
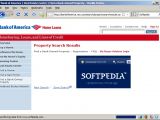
Cross-site scripting weaknesses have been discovered in two websites belonging to the Bank of America and U.S. Bank. The flaws facilitate potential phishing attacks, because they allow attackers to inject IFrames, hijack sessions, or prompt arbitrary alerts.
Cross-site scripting, more commonly known as XSS, is a class of vulnerabilities typically affecting web applications, which facilitate arbitrary code injection into pages. They are the result of poor programming, manifested by the failure to properly escape input passed into web forms.
The flaws discovered in the websites of the U.S. Bank and Bank of America are referred to as non-persistent XSS weaknesses and are the most widely spread type in the class. This means that, while they can be exploited through URL manipulation, the injected code does not persist if the URL is changed.
Even if the actual risk posed by these weaknesses is lower than that of persistent XSS flaws, they are still dangerous for various reasons. For example, such malformed URLs can be used in complex phishing campaigns, significantly raising their credibility. This is because users are, obviously, more likely to visit unsolicited links pointing to domains they trust.
The latest vulnerabilities have been reported and documented by a grey-hat hacker calling himself Methodman, who is a member of Team Elite, a group of programmers and security enthusiasts. In his proof-of-concept (PoC) attacks, he outlines how attackers can sniff session cookies (text files stored by websites inside browsers in order to automatically authenticate users).
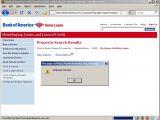
However, even if Methodman limited his PoCs to session hijacking attacks, this is not the only unauthorized action cybercrooks can perform through these flaws. As demonstrated by the screenshots we took ourselves, IFrame injection is also possible. IFrame is an HTML element, which allows loading externally hosted content into a web page.
IFrames are heavily used in most web-based attacks, because they can be entirely hidden. Hidden IFrames are generally used by malware distributors to load malicious JavaScript code in the background. However, styles can be applied to them fairly easy, which is a great advantage for phishers. For example, such an IFrame could be used to inject a rogue form, which asks for the visitor's financial details, and be made to look as being part of the legit page.
At the time of writing this article, the XSS weaknesses on the U.S. Bank and Bank of America websites remain active.

 14 DAY TRIAL //
14 DAY TRIAL //