A new threat affecting ATM (automated teller machine) systems features security measures that allow interaction with it only at certain times, and permits cash withdrawal through direct interaction with the computer, without the need of a card.
The malware has been named Tyupkin by researchers at Kaspersky, who dissected a few samples. It runs on ATM systems from a single manufacturer with 32-bit Windows installed on them.
It appears that infecting the cash machines is done by breaking the physical security and gaining access to the computer inside. Tyupkin is then planted on the system by loading it from a bootable CD.
Interaction with the malware is protected
The actors using this malware have implemented certain security measures to ensure that only they have control over it.
One protection mechanism available is making it respond to commands only at certain times, when the crooks come to collect.
From Kaspersky’s observations, the Tyupkin responded to interactions only on Sunday and Monday nights by default.
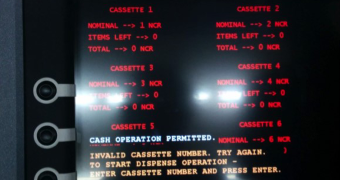
Furthermore, a session key code needs to be entered before the main menu is shown, where the attacker can see the cash cassettes and the number of banknotes available; a maximum of 40 can be extracted at a time.
The unlocking key needs to be generated based on a seed displayed on the screen, so only an individual that knows the algorithm behind the operation can reach the command menu.
If the wrong code is entered, then the malware disconnects from the local network, probably in an attempt to prevent remote investigation, Kaspersky believes.
Eastern Europe banks most targeted by Tyupkin attacks
Based on the compilation dates of the analyzed samples, it is believed that Tyupkin has been in use since around March this year.
However, multiple variants exist, authors adding anti-analysis capabilities (anti-debug and anti-emulation) along with the ability to disable McAfee Solidcore, a dynamic whitelisting application, on the infected machines.
The researchers say that during their investigation, most of the 50 ATMs affected were from banking institutions in Eastern Europe.
According to statistics pulled from VirusTotal, most of the Tyupkin submissions came from Russia. However, Kaspersky noticed that the malware reached other countries too, as infections were reported from the United States, India, China, Israel, France and Malaysia.
Security experts from the Russian antivirus vendor see this type of attack as a natural evolution from skimming, which relies on stealing card information when the client inserts it into a corrupted ATM. Cybercriminals are “moving up the chain and targeting financial institutions directly. The Tyupkin malware is one such example of attackers moving up the chain and finding weaknesses in the ATM infrastructure.”
The general recommendation for banks is to ensure that proper security measures are enforced both to the cashpoints and the environment they are placed in, with sufficient lighting and cameras monitoring all activity.
Demo of a real ATM being robbed using the Tyupkin malware:
 14 DAY TRIAL //
14 DAY TRIAL // 