Yesterday, several thousand Tumblr blogs were blogs were “defaced” with the aid of a worm that most likely exploited the service’s reblog feature.
Experts from security firm Sophos have determined that the attackers relied on a JavaScript code in order to trick victims into publishing a racist message on their own Tumblr.
“It shouldn't have been possible for someone to post such malicious JavaScript into a Tumblr post - our assumption is that the attackers managed to skirt around Tumblr's defences by disguising their code through Base 64 encoding and embedding it in a data URI,” Sophos’ Graham Cluley explained.
The folks from Sophos weren’t the only ones to analyze the incident. Security researcher Janne Ahlberg believes that the attack is based on a stored cross-site scripting (XSS) vulnerability.
Tumblr representatives have stated that the issue has been resolved, but Ahlberg has found that the security hole – which is not difficult to locate – still plagues the website.
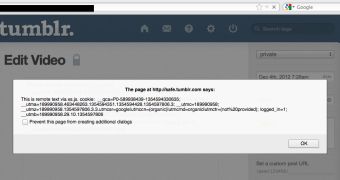
“I created a temporary Tumblr account using different browser, submitted a public post with stored XSS payload and visited the profile using Safari from another account and PC. The vulnerability seems to be valid,” the researcher explained on his personal blog.
The expert warns that if Tumblr doesn’t act on addressing this issue soon, it could be leveraged for even more severe attacks than this one.
Unfortunately, it appears that it takes Tumblr a long time to address security issues. Back in July, security researcher Riyaz Ahemed Walikar reported a similar vulnerability to the company and it took them more than 3 weeks to address it.
Furthermore, the hackers behind the Tumblr worm told Gawker that they also reported the flaw to the company around one week before turning to this unorthodox approach in order to get them to patch up the issue.
 14 DAY TRIAL //
14 DAY TRIAL //