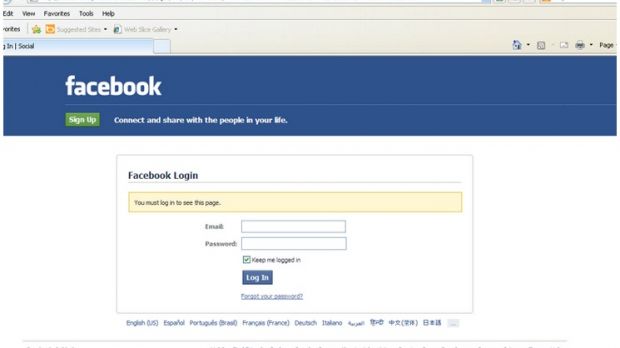
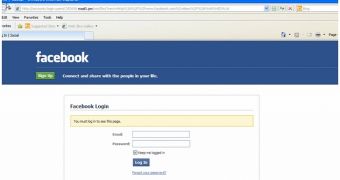
Security experts from Blue Coat have stumbled upon a number of shady Tumblr websites while analyzing a domain called maal1.pw. After a close look, researchers have determined that this domain is being used to host Facebook phishing pages.
Blue Coat believes that cybercriminals are most likely using Facebook to lure users to the Tumblr websites. It’s uncertain what tricks they’re using, but as most Facebook customers know, they have a lot of options.
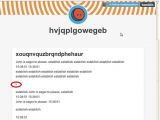
The Tumblr websites contain random words and randomly typed letters. However, they also contain a 1x1 pixel iFrame that retrieves a piece of JavaScript from a remote location (tumposthostingxqo.com).
Unfortunately, Tumblr doesn’t have any protection mechanisms in place to prevent users from inserting external JavaScipt links into their sites.
The script redirects users to a page on maal1.pw that’s designed to replicate the Facebook login page.
Additional technical details on this phishing campaign are available on Blue Coat’s blog.
 14 DAY TRIAL //
14 DAY TRIAL //