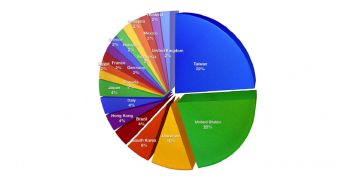
Security researchers from Trend Micro have released a paper called “IXESHE – An APT Campaign” in which they detail the attacks launched by cybercriminals against East Asian governments, electronics manufacturers and one particular telecoms company from Germany.
IXESHE (pronounced “i-sushi”) is different from other advanced persistent threat (APT) campaigns because its masterminds compromise company systems and use them as command and control (C&C) servers.
By leveraging this technique, they are able to mask their illegal activities and their malicious elements by mixing them up with the legitimate files that are already present on the overtaken server.
In one case, the C&C servers of the IXESHE campaign were hosted on the devices of a country from Eastern Asia. This allowed the cybercriminals to easily launch attacks against that particular country’s government.
The malware that powers the campaign infects a system by leveraging security holes in Adobe Acrobat, Reader and Flash Player.
The complete paper is available here.
 14 DAY TRIAL //
14 DAY TRIAL //