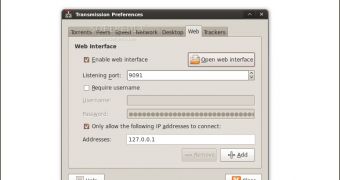
As you all know, Canonical's popular Ubuntu Linux distribution ships with Transmission as the default BitTorrent client. One of the newest features of Transmission is a web-based interface, accessible from your Internet browser. And though there aren't many users interested in or aware of this alternative way of managing torrents, it is enabled by default in Transmission's preferences.
Unfortunately, a pretty serious vulnerability in this new feature affects all Transmission versions prior to the just released 1.61. The CSRF (Cross-Site Request Forgery) hole was discovered by security researcher Mike Bailey and was documented on his blog. The Cross-Site Request Forgery attack lures users into opening web pages containing malicious requests that allow the attacker to perform various actions (password change, downloads, important information changes) on behalf of the unaware victim.
Mike Bailey better explains how this hole can affect a Linux machine: "Basically, it allows me to first change the download destination to one of my choosing, then download a torrent of my choosing. This is bad – I could force a user to download a new .bashrc file or overwrite their entire home directory." He also created a proof-of-concept to demonstrate how this works. Fortunately, the Transmission team was quick to respond and released the 1.61 version that fixes this vulnerability. Still, Canonical has yet to push the update through their channels, even though this is quite a serious security issue.
Mike Bailey also notes that a similar exploit was found in Azureus' (another popular P2P and BitTorrent client, now known as Vuze) web interface: "Nate McFeters talked about doing the same thing through an XSS hole in the Azureus web interface in his talk, "the Internet is Broken", at Black Hat 2008."
Download Transmission 1.61 right now from Softpedia.
 14 DAY TRIAL //
14 DAY TRIAL //