Basic security issues in the networked system regulating traffic flow in Michigan allowed a team of researchers to take control of about 100 traffic lights.
The experiment was conducted by a team led by J. Alex Halderman, computer scientist at the University of Michigan, with the approval of a local road agency.
They managed to intercept the communication between traffic sensors and controllers that communicate wirelessly, gaining complete control of the stoplights regulating the flow of vehicles on the road.
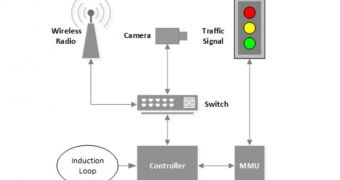
In many cities across the United States the traffic flow is managed through intelligent wireless systems that rely on sensors buried below roadways to detect the cars. They send the data to a controller, which changes the traffic light.
According to a paper researchers presented at the Usenix security conference in San Diego this week, in some cases, the controllers are part of an interconnected system and may communicate via radio frequency.
Halderman and his team found that the controllers could be set up remotely, via an FTP connection to a configuration database. However, accessing them this way barely benefits from any protection at all.
“An FTP connection to the device allows access to a writable configuration database. This requires a username and password, but they are fixed to default values which are published online by the manufacturer. It is not possible for a user to modify the FTP username or password,” say the researchers in the paper.
During the experiment, it was discovered that the traffic regulation system was riddled with elementary security flaws. The team found that the network could be easily accessed because encrypted communication was not available; controllers did not benefit from secure authentication and they were also vulnerable to known exploits.
Apart from the stoplight management devices, an adversary could also attack sensors and the video cameras, which usually feature pan, tilt, and zoom control capabilities and send visual traffic information to the central server.
The study shows that attackers can infiltrate the traffic network through the wireless infrastructure, and with no encryption in place or concealment of the SSID, it is enough to reverse engineer the proprietary communication protocol or to use the same type of radio hardware employed in the traffic system.
“Due to the lack of encryptions, any radio that implements the proprietary protocol and has knowledge of the network’s SSID can access the network,” explains the paper.
The results of such an intrusion are easy to predict. The actions supported by the controller include not just changing the lights based on an “if-then-else” logic, but also freezing them.
Among the possible types of attacks include denial of service (setting all lights to red) leading to traffic congestion, which can also be achieved in a more subtle way, by manipulating the timings of an intersection, leaving the impression of a poorly managed road network.
Also, attackers can control the lights as they wish, changing colors according to their needs (setting them to green for a specific route).
A similar experiment, with the same dire consequences, was carried out by IOActive CTO Cessar Cerrudo, who presented his findings at DefCon hacker conference in Las Vegas earlier this month.
 14 DAY TRIAL //
14 DAY TRIAL //