A malicious email campaign targeting mostly users in Australia with TorrentLocker ransomware has brought its operators a hefty revenue of about $224,000 / €190,000 in one month.
TorrentLocker is a known threat that is designed to encrypt certain files on the affected system, serving the victim with a ransom notification when the data is locked. The initial fee requested by the cybercriminals is 1.7 BTC ($470 / €398) but it doubles up if the payment is not made within four days from the encryption.
Cybercriminals' wallet involved in over 1,200 transactions
Security researchers at Trend Micro found that more than 98% of the recipients of the malicious messages were from Australia, although they observed that the same campaign was run in other parts of the world, too.
They managed to identify one bitcoin wallet address that is believed to have been set up by the cybercriminals. On Sunday, Trend Micro saw that it was involved in 1,223 transaction and that it received 810 BTC between November and December 2014.
From the wallet created to collect the ransom, the attackers then transfer the digital currency to different other addresses, until the money reaches the intended beneficiary.
Chaining the transactions is designed to make tracing more difficult. To the same effect, the payment is made through TOR anonymity network, which can be accessed by the victim without having to install the service, by using Tor2Web proxy.
Fraudulent messages pass spam filter verification
Security researchers say that the messages could pass the verification of some spam filters, thus finding their way easier to the victims.
“In order to increase the chance of delivery by spam filters, these spam runs were authenticated by the Sender Policy Framework (SPF). For example, in one spam run, the sending domain was send-nsw-gov[.]org, which could pass the SPF check – and thereby increase the chance of delivery by some spam filters,” said in a joint blog post Paul Pajares (fraud analyst at Trend Micro) and Christopher Ke, web threat researcher at Deakin University.
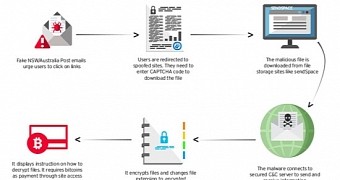
The operation relies on social engineering, fooling recipients into accessing a malicious link that leads to downloading the ransomware. To ensure that victims pay the fee, the malware also deletes the file backups created automatically in Windows by the Volume Shadow Copy service.
The scam follows a simple pattern: an email claiming to come from a trusted sender (in this case New South Wales government and Australia Post) informs the recipient that a document of urgent interest is available at a link provided in the message, where a file is offered for download.
The file, hosted on SendSpace.com, is actually the malware, and when executed, it proceeds to encrypt the data on the computer.
Identifying the operators is difficult
The cybercriminals invested the effort to make the scam look legitimate. Apart from spoofing the official pages, they also integrated a CAPTCHA gate, which is a security measure against bots, and also has the role of eliminating suspicion of malicious activity.
The servers hosting the fake web pages benefited from more advanced mechanisms to hide their locations, Trend Micro said in a report released on Monday. The time-to-live of the DNS records was of just one hour, so upon taking them down all cached domain name resolutions would disappear in that period of time.
On the same note, the web and the DNS services were on the same machine, the cybercriminals registered the malicious web addresses with the real information of the organizations they spoofed and all landing pages used different IP addresses.
All this makes extremely difficult to identify the threat actor or to correlate it with other activities.
 14 DAY TRIAL //
14 DAY TRIAL //