A malicious exit server in the anonymity network Tor has been found to distribute a new family of malware researchers dubbed OnionDuke because of its connection to the group behind the cyber-espionage tool MiniDuke.
This type of attack is an uncommon one and has been discovered by Josh Pitts, penetration tester at Leviathan Security.
Malicious DLL poses as GIF image
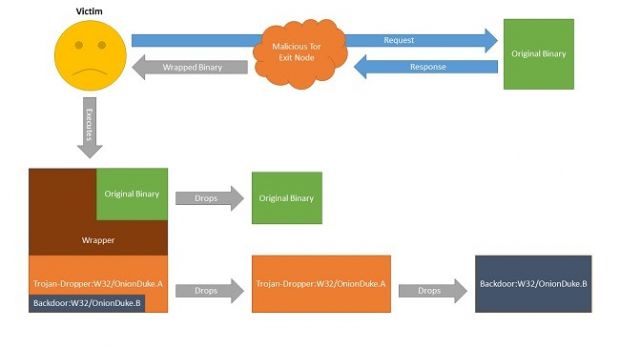
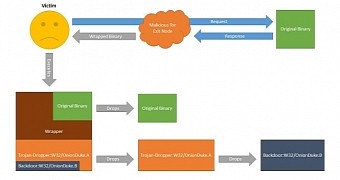
He found that the bad exit node would modify the uncompressed binaries passing through it by repackaging them and adding a malicious executable in the process; this method would help the attacker bypass integrity checks associated with the original file.
Security researchers at F-Secure studied this new malware distribution technique and confirmed the information presented by Pitts, offering details about how the payload was executed, its communication with the command and control (C&C) server and the embedded functionality.
They found that as soon as the binary downloaded through the bad TOR server is launched, it executes both the original executable and the second one, which is a malware dropper. This action would not raise any suspicions to the victim since the legitimate software component is added to the system.
Artturi Lehtiö analyzed the behavior of the dropper and noticed that it contained an encrypted DLL posing as a GIF image. After decrypting the DLL, the dropper would store it on the disk and execute it.
The chain of malicious activities continues with decrypting configuration file and trying to connect to a hard-coded C&C server that would deliver further instructions to the malware.
Malware component reveals connection with MiniDuke group
Several OnionDuke components have been identified during the analysis, revealing its capabilities. Stealing credentials is on the list of intended purposes for the malware, and in order to achieve persistence on the affected system, the author added routines for detecting the presence of security products (antivirus, firewall).
It was in one of these components that the researchers found the connection between OnionDuke and MiniDuke, which consisted in a C&C domain that was registered in 2011 under the alias John Kasai and was used for registering others two weeks later, employed by the espionage tool.
“This strongly suggests that although OnionDuke and MiniDuke are two separate families of malware, the actors behind them are connected through the use of shared infrastructure,” Artturi Lehtiö wrote in a blog post on Friday.
According to the researcher, there is evidence that OnionDuke has been used in targeted attacks against European government agencies.
Downloading non-encrypted executable files through Tor is a risky action because the identity of the exit node is not known; Lehtiö suggests using a VPN connection that would encrypt the connection end-to end.
 14 DAY TRIAL //
14 DAY TRIAL //