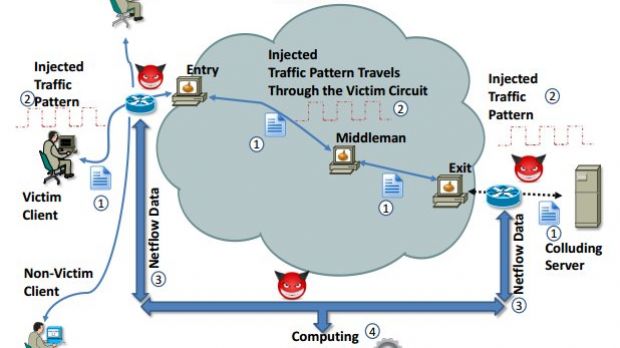
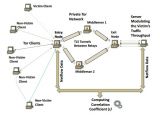
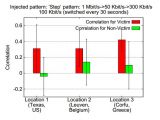
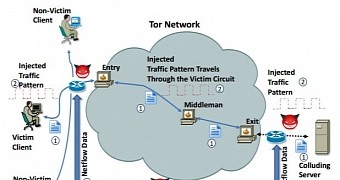
A recent paper about the possibility to de-anonymize users on Tor (The Onion Router) anonymity network caused some ruckus online, but the maintainers of the project stepped in and calmed things down saying that the false positive rate make this type of attacks useless.
Based on six years of research, professor Sambuddah Chakravarty from the Indraprastha Institute of Information Technology in Delhi issued a paper revealing that the IP address of 81% of TOR users can be learned through traffic analysis collected by Cisco routers through NetFlow technology.
False positive rate is essential in the research
Chakravarty said in the paper (On the Effectiveness of Traffic Analysis Against Anonymity Networks Using Flow Records) that under laboratory conditions all anonymous sources have been accurately revealed. When tested in the wild, the accuracy dropped to 81.4% and a false negative rate of 12.2% was recorded.
The false positive rate was of 6.4%. According to Roger Dingledine, Tor Project leader, this value is highly important, because it demonstrates that at a large scale, the entire attack would be like finding the needle in the hay stack and make it inefficient.
“The discussion of false positives is key to this new paper too: Sambuddho's paper mentions a false positive rate of 6%. That sounds like it means if you see a traffic flow at one side of the Tor network, and you have a set of 100000 flows on the other side and you're trying to find the match, then 6000 of those flows will look like a match. It's easy to see how at scale, this ‘base rate fallacy’ problem could make the attack effectively useless,” says Dingledine in a blog post on Friday.
He also points out that this is not the first traffic confirmation experiment and it does not supersede any of the previous ones.
A large network is difficult to measure
Chakravarty’s work relies on identifying similarities in the traffic flow patterns entering and exiting the Tor network. The NetFlow data is not refined enough, and to balance this disadvantage, the attack type proposed by the researcher requires a server controlled by the attacker “that introduces deterministic perturbations to the traffic ofanonymous visitors.”
This could be part of a nation state project designed for observing the traffic passing through the Tor exit servers at various points.
In return to this, Dingledine said that the amount of the Internet the attacker can measure or control is also a very important aspect since this is directly tied to the efficiency of the project as well as to the financial effort required. The larger the network, the less successful the attack.
According to the Tor Project leader, users still have no reason to fear that their identity can be revealed when using Tor.
 14 DAY TRIAL //
14 DAY TRIAL //