A grey-hat hacker going by the online handle of Vektor has disclosed several cross-site scripting vulnerabilities in several pages of the IFPI website. According to the report, Sage Pay, the payment service provider used by the IFPI and many other websites, is actually responsible for some of the flaws.
Vektor is a member of a free software development group called Team Elite and has recently discovered XSS vulnerabilities in the websites of several organizations representing the film, music and software industry, such as MPAA, RIAA and BSA. While in the process of targeting the International Federation of the Phonographic Industry (IFPI), the hacker thinks he might have stumbled on something much bigger.
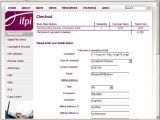
Most of the cross-site scripting vulnerabilities in the IFPI website are caused by the shopping cart script, which allows visitors to buy various publications and reports. In addition to being able to modify the total price value displayed by the cart, an IFrame can also be injected into the billing information form.
Furthermore, fake products can also be created through cross-site scripting, the hacker exemplifying this by offering to sell toilet paper imprinted with "RIAA" and modifying the download page for a free application to display rogue and potentially dangerous information.
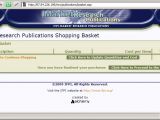
An IFPI sub-site called Market Research Publications also suffers from the same shopping cart flaws and is susceptible to IFrame injection. After closely inspecting these vulnerabilities, however, Vektor has concluded that most of them originate in the Sage Pay system, the payment service provider employed by the IFPI.
"A problem with the Sage Pay payment system makes all the websites using it vulnerable to cross-site scripting and fraud," the hacker writes in an e-mail to Softpedia. He has refused to disclose any particular details until the issue gets fixed, but he has informed us that the Sage Pay management has been alerted of the problem.
Sage Pay, previously known as Protx, is a large payment service provider based in the UK. According to its own website, the company services over 25,000 customers and handles some four billion transactions every year. "Sage pay is also audited annually under the Payment Card Industry Data Security Standards (PCI DSS) and is a fully approved Level 1 payment services provider, which is the highest level of compliance. We are also active members of the PCI Security Standards Council (SSC) that defines card industry global regulation," the company says.
At the time of writing this article, many of the vulnerabilities on the IFPI website were still active, even though they were originally disclosed three days ago. Regarding the Sage Pay situation, we will return with more information as and if it becomes available.

 14 DAY TRIAL //
14 DAY TRIAL //