The Intercept’s Glenn Greenwald and Ryan Gallagher have published another report based on information stolen by Edward Snowden from the US National Security Agency. The latest report highlights the technologies that enable the intelligence agency to perform “industrial-scale exploitation” of computer networks.
It turns out that the NSA has automated processes in place that enable them to plant malware on millions of computers worldwide. Documents obtained by Snowden show that the British intelligence agency GCHQ has played an important role in developing these systems.
The NSA’s tactics are similar to the ones used by cybercriminals. In some cases, it has set up a fake Facebook server and has used the social media website to distribute a piece of malware capable of stealing data from infected computers.
The agency has also relied on spam campaigns to distribute software capable of recording audio and taking pictures via the computer’s webcam.
In 2004, there were around 100-150 malware implants. However, as the Tailored Access Operations (TAO) unit recruited hackers and developed new tools, the number of implants reached tens of thousands.
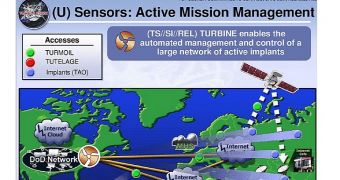
Since it’s impossible to manage the malware implants manually, the NSA has developed a solution called TURBINE. This system is capable of managing active implants, enabling the agency to conduct “industrial-scale exploitation.”
TURBINE is said to be part of a broad NSA surveillance initiative dubbed “Owning the Net.” And in case you’re wondering how much money goes into the project, the NSA has requested a $67.6 million (€48,6 million) budget for it last year. There is a wide range of implants utilized by the NSA. For instance, UNITEDRAKE is used to gain complete control of a device.
UNITEDRAKE has a number of plug-ins, each designed for a specific purpose. CAPTIVATEDAUDIENCE is for recording conversations via the computer’s microphone, GUMFISH is for hijacking the webcam, FOGGYBOTTOM for exfiltrating Internet data (including browsing history and passwords), and GROK is for capturing keystrokes.
And if you think that encryption tools can protect you against such malware, you are wrong. These threats are designed to circumvent such protections by capturing the information before it’s encrypted.
The NSA has used these capabilities to monitor not only terrorists and extremists, but also system administrators working for foreign ISPs and phone companies. These system admins are considered by the agency a “means to an end.”
The files on which this latest report is based are available on The Intercept.
 14 DAY TRIAL //
14 DAY TRIAL //