At the Kaspersky Security Analyst Summit in Punta Cana, researchers have presented the details of the advanced cyber espionage campaign dubbed “The Mask.”
When it first mentioned The Mask (also known as Careto), Kaspersky noted that the cybercriminals spoke a language that was rarely associated with threat actors. They’re right. It’s not often that we hear of sophisticated operations conducted by individuals who speak Spanish.
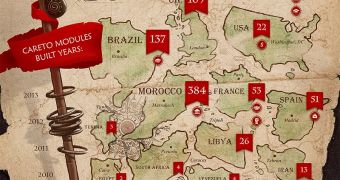
According to researchers, The Mask campaign has been ongoing since at least 2007, targeting government agencies, energy companies and other high-profile organizations spread out across a total of 31 countries in the Americas, Africa, Europe and the Middle East.
More than 380 unique victims have been identified in countries such as Algeria, Argentina, Bolivia, Belgium, China, Brazil, Colombia, Cuba, Costa Rica, Egypt, France, Germany, Guatemala, Gibraltar, Iran, Iraq, Malaysia, Libya, Mexico, Morocco, Pakistan, Norway, South Africa, Poland, Spain, Switzerland, Turkey, Tunisia, the UK, the US and Venezuela.
The attackers have a large arsenal of cybercrime tools at their disposal, including a bootkit, a rootkit, malware for Mac OS X and Linux, and possibly even Android and iOS variants of sophisticated threats. One of the exploits they’ve leveraged in their operations is CVE-2012-0773, which targets Flash Player.
The sophisticated malware is distributed with the aid of spear-phishing emails sent to victims. These emails contain links to websites that host exploit kits. Depending on the victim’s system configuration, an appropriate type of malware is served.
Interestingly, the threat actors have developed an attack that’s specially designed against Kaspersky’s solutions.
The cybercriminals’ main objective is to collect sensitive information from the networks of government institutions, energy, oil and gas companies, diplomatic offices and embassies, research organizations and even activists.
“Several reasons make us believe this could be a nation-state sponsored campaign,” noted Costin Raiu, director of the Global Research and Analysis Team (GReAT) at Kaspersky Lab.
“First of all, we observed a very high degree of professionalism in the operational procedures of the group behind this attack. From infrastructure management, shutdown of the operation, avoiding curious eyes through access rules and using wiping instead of deletion of log files,” Raiu explained.
“These combine to put this APT ahead of Duqu in terms of sophistication, making it one of the most advanced threats at the moment. This level of operational security is not normal for cyber-criminal groups.”
Kaspersky said the command and control (C&C) servers were shut down sometime in January 2014, during their investigation.
For additional information on The Mask, check out the FAQ published by Kaspersky or the detailed report called “Unveiling ‘Careto’ – The Masked APT.”
 14 DAY TRIAL //
14 DAY TRIAL //