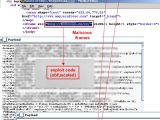
Researchers from IT communications security company Websense warn that the website of Portugal's Embassy in India has been compromised by malware distributors and is currently attempting to run exploits for no less than six vulnerabilities in different software packages.
Several rogue IFrames have been injected into the source code of the embassy's website. They are used to load obfuscated JavaScript code from external Chinese domain names associated with cyber-criminal activities.
The scrambled code subsequently tries to execute several exploits against some applications installed on the visitors' computers. More specifically, the targeted vulnerabilities are: VMLRender (MS07-004), 2007 WinZIP FileView ActiveX CreateNewFolderFromName method (CVE-2006-6884), Apple QuickTime RTSP (CVE-2007-0015), MS Internet Explorer WebViewFolderIcon (CVE-2006-3730), Internet Explorer (MDAC) Remote Code Execution (MS06-014), and Adobe Reader PDF exploit (CVE-2007-5659).
"The Embassy of Portugal in India provides visitors with brief information about bilateral relations between the countries, related news and events, tourism, and consular information," the Websense analysts explain. "Websense ThreatSeeker Network has been tracking how this type of attack is carried out successfully over such reputable Web sites, targeting their peers and other visitors," they note.
It's safe to assume that if one of those exploits is successful, more malware will be dropped on the victim computers. It appears that the Embassy has been notified of the attack, because its website is, at the time of writing this article, completely inaccessible. It is likely that the technicians are in the process of cleaning the pages and restoring it.
This incident follows after only a few days ago we reported that the Embassy of Ethiopia in Washington and Azerbaijan's embassies in Hungary and Pakistan had had their web presences tainted in a similar manner. Other past attacks involved websites belonging to the Indian Embassy in Spain, the U.S. Consulate in St. Petersburg, the French Embassy in Lybia, the Syrian Embassy in London, the Dutch Embassy in Moscow, or the Embassy of Brazil in India.
This clearly reflects a trend of targeting websites associated with diplomatic missions and that could be caused by the nature of their visitors. Many of the people accessing such resources are businessmen or representatives of multinational companies, generally individuals with a good financial situation that need travel or stay visas and such. Their computers represent the most profitable targets for cyber-criminals looking to steal some banking details.
In addition, the presence of exploits for vulnerabilities that have already been fixed by software vendors suggests that users in general are slow to deploy patches. If this wasn’t true, such attacks would not be very successful and therefore unprofitable to instrument.

 14 DAY TRIAL //
14 DAY TRIAL //