A new tool was open-sourced by Google on Tuesday, aiming at improving the efficiency of automated web security scanners by evaluating them with patterns of vulnerabilities already seen in the wild.
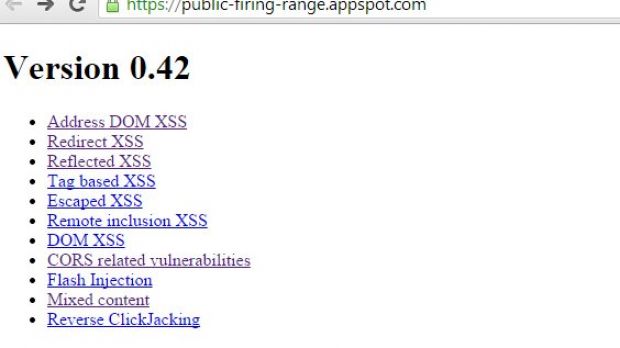
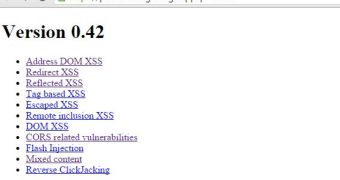
Named Firing Range, the utility is basically a synthetic testing ground mostly for cross-site scripting (XSS) flaws, which are the most frequent bugs in web apps; other types of vulnerabilities (reverse click-jacking, Flash injection, mixed content, and cross-origin resource sharing) are also included, although to a much lesser extent.
A tool for testing web app security scanners
The tool has been developed by Google while working on Inquisition, an in-house web app security scanning tool, which includes support for the latest HTML 5 features and has a low false positive rate.
Firing Range is a Java application that has been built on Google App Engine and is available on GitHub. It includes patterns for the scanner to focus on different XSS bugs, such as DOM-based, redirected, reflected, tag-based, escaped and remote inclusion.
“Our testbed doesn’t try to emulate a real application, nor exercise the crawling capabilities of a scanner: it’s a collection of unique bug patterns drawn from vulnerabilities that we have seen in the wild, aimed at verifying the detection capabilities of security tools,” writes Google security engineer Claudio Criscione in a blog post.
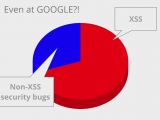
At the Google Testing Automation Conference (GTAC) last year, Criscione said that about 70% of the security bugs detected at Google were XSS. Going through the information manually is both exhausting and counter-productive for the researcher.
Automated XSS finding is more productive
Security experts at Google believe that an automated approach involving testing for various known contexts and attack vectors an app may be susceptible to is more productive.
Developers and researchers can check a deployed variant of Firing Range and contribute with feedback on how to improve the tool.
The testbed is not developed by Google in its entirety, as researchers at the Politecnico di Milano are also credited for their efforts.
At the beginning of the month, Google open-sourced another security-related tool called Nogotofail. This is intended for checking the security of the traffic in the network, more specifically for bugs in the encryption protections applied through HTTPS, by offering a man-in-the-middle (MitM) test environment.
It can help developers verify if their apps are safe against known SSL/TLS vulnerabilities, such as the recently discovered POODLE (Padding Oracle On Downgraded Legacy Encryption).
The tests included refer to common SSL certificate verification problems, HTTPS and TLS/SSL library bugs, SSL and STARTTLS stripping issues, and clear text problems.
 14 DAY TRIAL //
14 DAY TRIAL //