Over the weekend, visitors of TeslaMotors.com could no longer see the presentations of the latest Tesla models, as hackers managed to hijack the DNS records that pointed to the correct webserver hosting the website and changed them to direct to a machine under their control.
The hackers also modified the mail exchanger (MX) records, which are a resource of DNS (domain name system), thus being able to receive any email delivered to the company. This allowed them to take control of the Twitter accounts of the company and its CEO, Elon Musk.
Hackers draw attention to two Twitter accounts
It must be noted that the website was not hacked, as the perpetrators did not access the hosting web server; instead, the attack was on the registrar (Network Solutions), which keeps the domain name records.
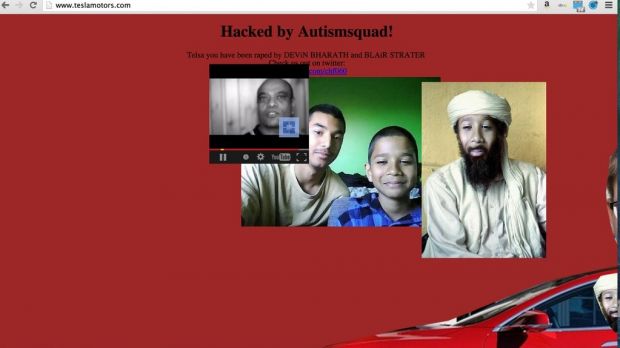
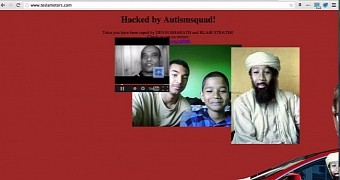
On Saturday, TeslaMotors.com showed the images and messages the attacker had uploaded on its server. The illegal website design foisted by the attackers was simplistic and featured pictures of some people and a Tesla car.
At the top of the page there was a message saying that “Autismsquad” was responsible for the attack, giving out two Twitter accounts, one of them being now suspended, the other belonging to someone known on Twitter as “r00t,” who apparently had nothing to do with the incident.
Along with the website trouble, the Twitter accounts of both the company and its CEO were compromised, and the attackers used them to promote a fake offer of free Tesla cars for anyone who called given phone numbers.
One of the numbers belonged to “r00t,” who said that at one point he was receiving about five calls every minute. In another tweet, he revealed he was called by the attackers themselves, who made threats.
2FA could have prevented the hijack of the social media profiles
The name of Tesla’s main Twitter account was changed to “#RIPPRGANG” and its more than 550,000 followers were delivered spam messages with the bogus “free car” offers, at the same time promoting other Twitter accounts.
Getting control of the social media accounts was most likely possible because the two-factor authentication (2FA) protection measure was not turned on. 2FA enables logging in based on additional verification that is under a code received by the owner on a device in their possession.
With access to the incoming email messages, the perpetrators initiated a “lost password” procedure for the Twitter assets and waited for the confirmation message to be delivered.
The entire incident was short lived, and at the moment, TeslaMotors.com, its Twitter account and Elon Musk's account on the same service are handled by their rightful owners.
Again, There is no free car, I did not hack Elon Musk or Tesla's Twitter account. A Finnish child is having fun at your (and my) expense.
— r000t (@rootworx) April 25, 2015
Currently receiving about 5 phone calls a minute about a "free Tesla". A free car is NOT being offered, please stop calling.
— r000t (@rootworx) April 25, 2015
 14 DAY TRIAL //
14 DAY TRIAL //