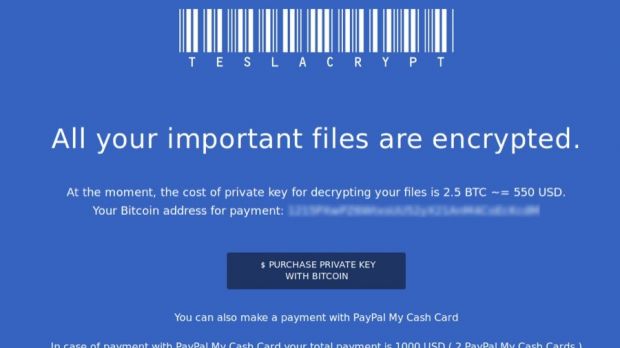
Asking for payments that would not pass the 2.5 bitcoin ($600 / €520) mark, the creators of TeslaCrypt, also seen under the name of AlphaCrypt, made a little over $75,500 / €66,500 between the months of February and April of this year.
The amount may not appear significant, compared to the profit pulled by older ransomware with file encryption capabilities, such as CryptoWall or CryptoLocker, but it shows that this type of threat continues to be an efficient way to fill cybercriminals’ pockets.
Malware affected people from all over the globe
TeslaCrypt was in the media spotlight in March for its choice to lock data belonging to popular games in order to force the victim to pay the ransom fee, which varied depending on the method selected.
For instance, buying the decryption key with bitcoin digital currency was cheaper than via the PayPal My Cash service, when the fee increased to $1,000 / €880, because the attacker had to further launder the money in order to get it, which involves additional costs.
Security researchers at FireEye tracked the bitcoin money paid by the victims during the roughly two-month period and learned that 163 people gave in to the cybercriminals’ demands.
“The victims were spread across the globe from students in Iran and Spain to regular folks in the United States, Brazil, Argentina, Germany, Croatia and Mongolia,” says Nart Villeneuve in a blog post published on Friday.
The malware is indiscriminate about its victims, as they ranged from individuals to organizations, even non-profit ones. Villeneuve says that an entity contributing to efforts for curing blood cancer and small businesses were impacted by the threat.
Cybercriminals have a heart, too
However, it seems that in many cases the payment demanded by the crooks was too much and the victims would simply resign at the thought that their data was lost forever.
According to the information from FireEye, the number of victims they counted was 1,231, but only 13% of them purchased the decryption keys.
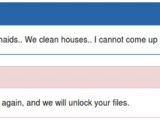
It appears that the crooks can be reasoned with, as in three cases, they provided the data unlock keys for free, after the user pleaded with them via a message center set up specifically for communication with the victims. Other times, the crooks found it in their heart to reduce the payment.
The support service, located in TOR anonymity network, recorded interaction with 263 individuals.
The researchers also say that one user managed to trick the cybercriminals into believing that he made a bitcoin payment that did not appear in the ledger.
Although this group seems flexible, there is always the possibility that they shut their messaging service or close shop and move to other means of making money, leaving affected users with their data locked.
An easy way to make sure that this type of menace is easily dealt with is to update software on the system to the latest versions, and most importantly, create file backups and store them in a safe place with minimum or zero interaction with the main computer.
Security researchers from Cisco have developed a decryption tool for TeslaCrypt, which is available free of charge.
 14 DAY TRIAL //
14 DAY TRIAL //