Researchers have recently revealed the existence of the Heartbleed bug, an OpenSSL vulnerability that can be exploited to intercept private keys, usernames, passwords and other sensitive information.
Since the bug has been around for the past couple of years, many vendors are rushing to patch their installations. In the meantime, security experts are trying to find out which services are still vulnerable.
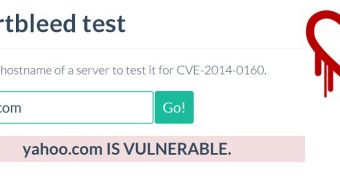
Security expert Filippo Valsorda has developed a simple online application that allows users to test if a certain server is vulnerable to Heartbleed attacks. Users simply have to enter the server’s hostname and they’re told if the service runs an unpatched version of OpenSSL.
Security expert Mustafa Al-Bassam, a former member of the notorious LulzSec collective, has compiled a list of vulnerable websites from the Alexa top 1,000 sites.
Of the top 1,000 sites, 512 have no SSL, 440 are not vulnerable, while 48 are. The list of 48 websites includes Yahoo, Imgur, Stackoverflow, Kickass Torrents, Flickr, Outbrain, Stackexchange, Web.de, OKCupid, XDA Developers, Scoop.it, DuckDuckGo, Eventbrite, WeTransfer and a number of popular adult websites.
Only 5 of the top 100 Alexa websites are vulnerable. These are Yahoo, Imgur, Stackoverflow, Kickass.to and Flickr.
Al-Bassam has highlighted the fact that the results might not be 100% accurate, but his experiment does provide some information on what types of services are impacted.
Fox IT has published indicators of compromise for the Heartbleed bug to help organizations in determining if they are vulnerable.
“It is possible to detect successful exploitation of this vulnerability by inspecting the network traffic. We have developed Snort signatures to detect succesful exploitation of the ‘heartbleed bug’. The rules apply on all ports which might generate some false positives,” Fox IT noted in its advisory.
The researchers who discovered the vulnerability have highlighted that these attacks don’t show up in any logs. Furthermore, while IPS and IDS solutions can be programmed to detect malicious attempts, attacks can only be thwarted if heartbeat requests are blocked completely.
OpenSSL version 1.0.1g has been released to address the vulnerability, which is caused by an implementation problem in the OpenSSL cryptography library, not a design flaw in SSL/TLS. The latest version is available for download on the website of the OpenSSL project. You can also download OpenSSL 1.0.1g from Softpedia.
CloudFlare, The TOR Project, Ubuntu, Red Hat and others say they’ve patched the vulnerability last week, before the existence of the bug was made public. It’s possible that other major companies have done the same.
 14 DAY TRIAL //
14 DAY TRIAL //