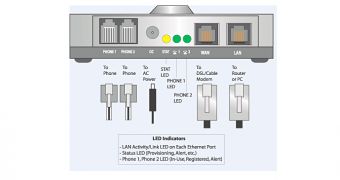
A new whitepaper published by software development company TransNexus reveals that a vulnerability in a widely utilized Analog Telephone Adapted (ATA) allows hackers to steal Session Initiation Protocol (SIP) credentials. Hundreds of thousands of SIP subscribers are believed to be affected.
Experts say that the stolen credentials can be used for wholesale telecom fraud.
The attacks described by TransNexus are problematic not only for consumers, but also for carriers.
When a device is hacked, it continues to function. This makes it highly difficult for a user to discover the breach.
On the other hand, the ATA device stops talking to the carrier’s configuration server. If the breach is discovered, the carrier must contact each individual victim to perform a factory reset.
“Once we discovered this particular vulnerability, we were able to get ahead of it pretty quickly," said Ryan Delgrosso, CTO at telecommunications provider Phone Power.
“We have seen other carriers with thousands of compromised accounts. We have since shared our findings with many other carriers, and have validated that this is happening across the industry, on a global scale. For many, this can be a nightmare scenario.”
The complete whitepaper, “VoIP Theft of Service: Protecting Your Network,” is available here (registration required).
 14 DAY TRIAL //
14 DAY TRIAL //