The greyhats at Team Elite, who were recently falsely blamed for hacking the MI5 website to steal the personal information of visitors, targeted the newspapers that denigrated them. Members of the outfit responded to the slanderous articles by revealing XSS weaknesses in the websites of The Daily Express and The Telegraph.
']['€AM€LiT€ (Team Elite) identifies itself as a group of programmers who develop "non-commercial solutions for one or more security-related problems." Aside from their many software projects, the security enthusiasts maintain a tracker of XSS weaknesses discovered by themselves in more or less high-profile websites.
Some of the affected websites belong to companies or organizations such as Kaspersky Lab, Avira, Symantec, McAfee, AVG, Eset, F-Secure, Trend Micro,Intel, eBay UK, PayPal, the U.S. Bank, Bank of America, RBS WorldPay, Visa, MPAA and RIAA.
On July 21, the outfit released an advisory regarding a cross-site scripting bug found in the MI5 website, which we subsequently reported on July 22. This was a non-persistent or Type 1 XSS flaw, which could have only been exploited if users were tricked into opening a malformed URL.
On July 30, British tabloid Daily Express reported the issue in the MI5 website, but significantly overhyped the threat and distorted the events. The story was picked up by other news agencies, which portrayed Team Elite as malicious hackers looking to attack the website's visitors and steal their personal information.
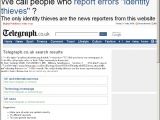
The Telegraph covered the incident in an article entitled "Identity theft hackers attack MI5 website." In response, Team Elite's Vektor, published details of a cross-site scripting vulnerability in the newspapers' website, which he demoed by altering a page to read, "Did you know our newspaper is full of lies? We call people who report errors 'identity thieves'? The only identity thieves are the news reporters from this website."
"I was wondering why does The Telegraph call us 'Identity theft hackers' when we are just reporting XSS bugs we find. So I searched their website for answers. This is the answer I found: their website is also vulnerable to same bugs," Vektor writes on Team Elite's website.
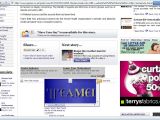
Another Team Elite member, [-TE-]-Neo, who originally disclosed the bug in the MI5 website, went directly after Daily Express. "I think reporters of The Daily Express need [to] improve their knowlegde [sic.] on how can a XSS flaw affect a website," he adds, before using a similar bug to show how an IFrame can be injected into the MI5 article page on the newspaper's website.
Team Elite members can be considered grey hat hackers, as they do not request for permission in advance of testing the websites for vulnerabilities. However, this is common practice when it comes to simple bugs, such as XSS. For example, the XSSed project has been maintaining an archive of such weaknesses since early 2007, many of which are still active.
We cannot agree with this kind of retaliation against The Telegraph or The Daily Express, but we are glad that the vulnerabilities were not used for any malicious purposes and their exploitation did not leave persistent rogue code behind.

 14 DAY TRIAL //
14 DAY TRIAL //