A new targeted phishing campaign has been observed by security researchers to focus on high level security professionals in technical companies, such as CTOs.
Since the US tax filing is approaching (deadline set on April 15), it’s no wonder that cybercriminals chose this theme to attract victims into downloading malware.
Messages are frequently updated
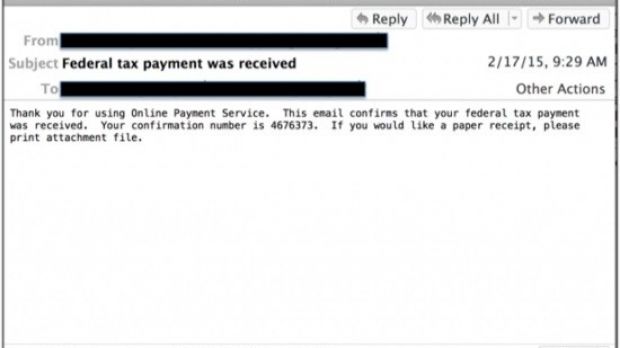
Researchers at Talos, Cisco’s security intelligence and research group, observed on Tuesday the deployment of the malicious campaign, which delivered emails with subjects related to different payment details and federal taxes.
The messages came with a malicious attachment disguised as a Word document laced with a macro (a script used for automating repetitive tasks) that bears instructions to download a malware dropper that funnels in Vawtrak banking Trojan.
According to the researchers, both the emails and the malicious Word file are constantly updated, different versions being recorded on Wednesday.
In the first wave of the campaign, the sender address was spoofed to appear from [email protected] or [email protected], informing that the tax payment was received. The newer version had different addresses for the sender and informed that tax information was not received.
It also included data on a large amount of money, probably in an attempt to incentivize the recipient to open the malicious document. Both samples informed that a paper receipt could be obtained by printing the attached file.
Cybercriminals make an odd target choice
Macros are disabled by default in Microsoft Office components but can be enabled manually by the user, which is what the cybercriminals instruct if the macro feature is turned off. Using them as a method of infection is not new and recently a flurry of similar incidents have occurred.
Depending on the activity type of a company, tech professionals, Chief Technology Officers (CTOs) in particular, are well aware of this and it comes as a surprise that they are targeted by the current phishing campaign.
Researchers analyzed the version of Vawtrak distributed this way and determined that it has the capability to capture user credentials for more than 100 online services, most of them belonging to financial institutions. However, “the list does include some phone providers and other online retail sites.”
Vawtrak has seen an increase in distribution lately. Security researchers at Trend Micro identified a different phishing campaign recently that distributed this piece of malware via macros in Word documents.
 14 DAY TRIAL //
14 DAY TRIAL //