An elaborated scheme has been set up by cybercriminals targeting Facebook users and preying their curiosity to direct them to dangerous online locations that deliver malware or try to subscribe them to premium-rate services.
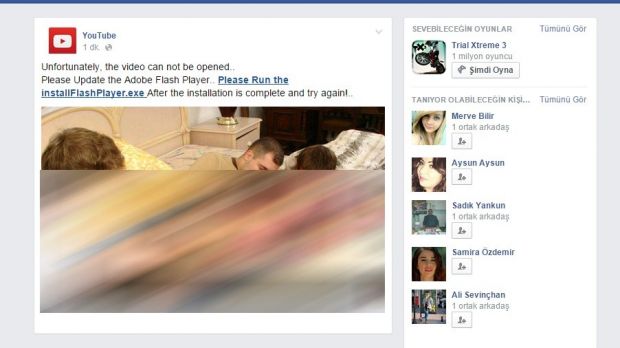
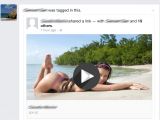
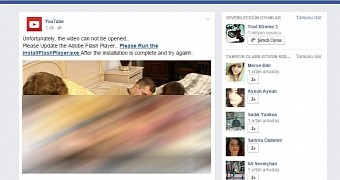
The scammers launched the malicious campaign over the weekend, using a classic “tag scam” as lure. In this particular case, the crooks send to the victim an enticing looking image posing as the thumb for a video, saying that some of their friends have been tagged in it.
Users are redirected several times until they reach the scam page
According to Bitdefender, the number of friends allegedly tagged in the video is always 20 and the lure is changed every time.
“The so-called video shows the goo.gl host underneath, which should raise some flags with more experienced users, as it is a URL shortening service and not a video hosting one,” says Bogdan Botezatu, senior threat analyst at Bitdefender.
Depending on the device used to access the fake content, the cybercriminals direct to different pages. In the case of mobile navigation, the potential victim is sent to the site of a premium rate service that attempts to subscribe them for at least €3 / $3.
Botezatu says that this occurs after several redirects, including one to a mobile traffic monitoring service that tells the crooks the number of individuals exposed to the scam and the amount that got trapped.
Classic Flash Player update trick leveraged
On Windows operating system, the redirect is to a page impersonating Facebook, which purports to serve a different video than the original one. Accessing the content is gated by the request to download a fake update for Flash Player.
The file is malicious and when launched, it proceeds to install two pieces of malware, one used to funnel in other threats and the other to spread the scam through the victim’s Facebook account.
Information from the researchers says that after tracking three different versions of the scam, they learned that behind the operation was a Turkish cybercriminal identified as “schwarzback.” As per the real-time analytics available in the scam pages, it seems that more than 5,000 social network users fell for the trick in less than one hour.
The domain hosting the scam may have been set up specifically for this purpose as it was registered on Saturday. Yesterday, it was still active.
 14 DAY TRIAL //
14 DAY TRIAL //