Symantec has made public the first excerpt of a draft describing an abstract security metasystem and laws of host security. Symantec's initiative is designed to elevate the level of discourse above definite features and implementations.
While Symantec has not directed the initiative at Microsoft, Al Hartmann - a Security Response Researcher with the Cupertino-based security company - did use the words "controversy" and "PatchGuard" in the same opening statement relating them to the problems emerging from "appropriate kernel security instrumentation."
With the host security metasystem and laws of host security, Symantec intends to "reach industry consensus on an architectural framework to guide designers of future host security subsystems and supporting instrumentation," reveals Hartmann, adding that Symantec is soliciting additional suggestions for the draft's finalization.
In this context, Symantec aims to get other parties in the security industry involved in the draft refinement process. "The primary goal is to agree upon an abstract architecture and guiding principles to frame the debate around operating system enabling of competitive host security services, without reference to specific features or implementations," added Hartmann.
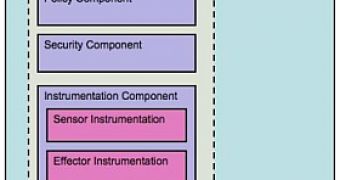
For this purpose, Symantec starts with the presumption that the security industry would best serve the worldwide computing community via an open security market. In this regard, Symantec suggested that a universal security monoculture (Microsoft's Kernel Patch Protection, or PatchGuard, in 64-bit Windows Vista - I added this example) would be synonymous with a decreased risk surface due to the existence of a variety of defensive solutions. The host security metasystem would be based upon three pillars: policy, security, and instrumentation.
"The instrumentation component provides both sensor and effector instrumentation to the security component. The security component uses sensor instrumentation to observe system behavior, internal logic to evaluate behavior patterns, and effector instrumentation to interdict malicious behavior. Security component actions are governed by security policy provided by the policy component," stated Hartmann.
In this initial presentation stage of Symantec's "Host Security Metasystem and Laws of Host Security," the security company outlined the sensor and effector instrumentation laws, referring to the monitoring and control interface for the host security metasystem.
1. Sensor instrumentation laws
1.1 Sensor observations shall be unobtrusive and performant 1.2 Sensor observations shall be unspoofable 1.2.1 A relevant occurrence shall be observed 1.2.2 An observation shall reflect an actual occurrence 1.3 Sensor observations shall be timely 1.4 Sensor observations shall be comprehensive
2. Effector instrumentation laws
2.1 Effector controls shall be unobtrusive and performant 2.2 Effector controls shall be unspoofable 2.2.1 A control action shall have been issued by the security component 2.2.2 A control action shall be executed as specified 2.3 Effector controls shall be timely 2.4 Effector controls shall be comprehensive
 14 DAY TRIAL //
14 DAY TRIAL //